
Declawing the Bear: CyCraft joins Round Two of the MITRE ATT&CK Evaluations
With over 1,200 cybersecurity vendors in the market today, only twenty-one of those selected were confident enough to participate in round two of the MITRE ATT&CK evaluations. CyCraft is excited to join the MITRE ATT&CK evaluations against the simulation of APT29/Cozy Bear.
For the majority of cybersecurity’s short history, security vendors have been hunting and labeling malware, which now numbers over 10 billion. As we venture further into the 21st century, modern adversary’s TTP (tactics, techniques, and procedures) leverage not just malware but also a diverse array of precise and adept techniques. In only seven years, MITRE ATT&CK has become THE codex for cybersecurity vendors and security analysts from finance, healthcare, energy, manufacturing, retail, and government to better understand modern adversarial behavior, especially as their tradecraft expands from information theft and fraud, to espionage, disinformation, and even sabotage.
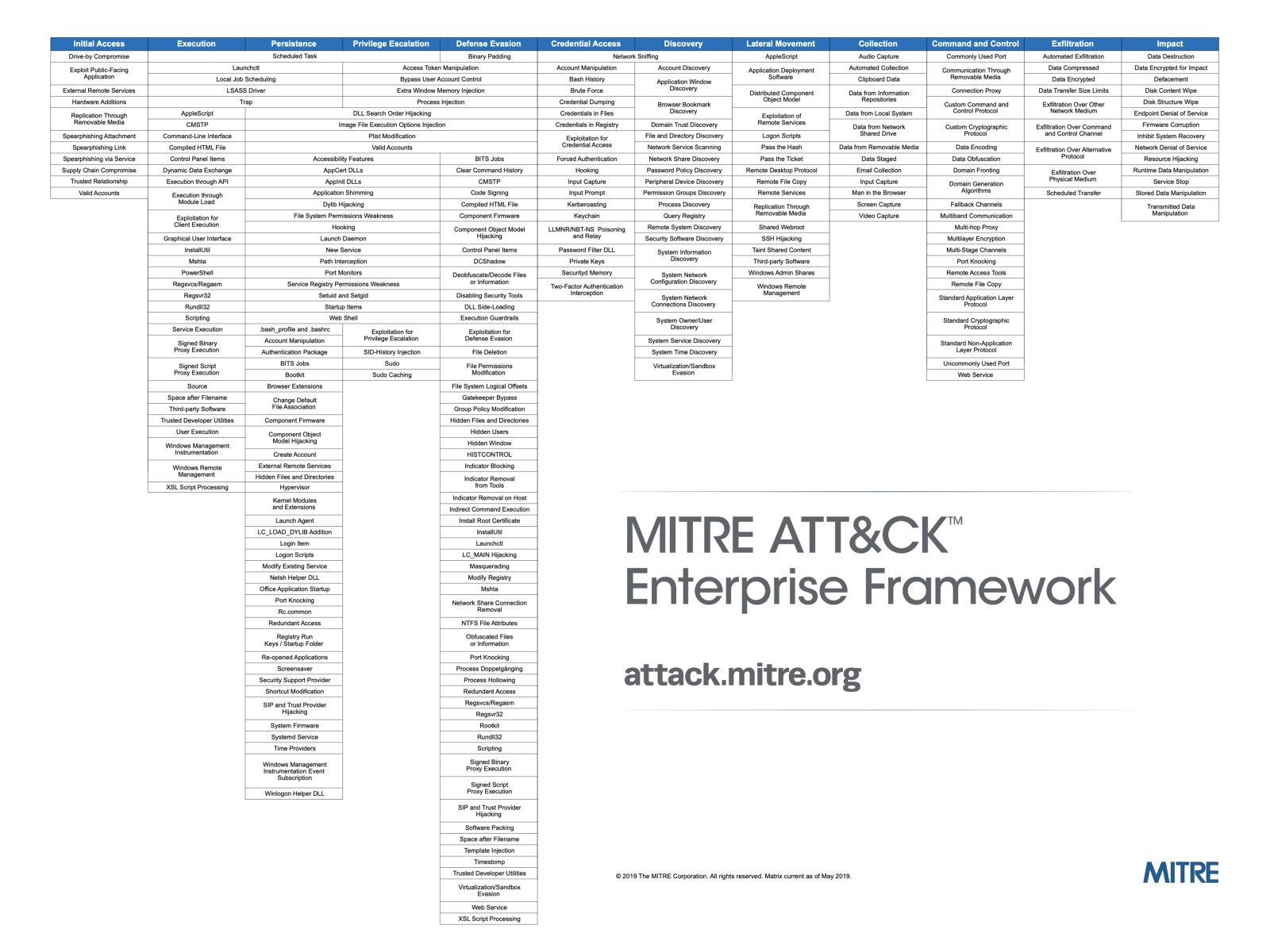
The most valuable thing MITRE ATT&CK has given the cybersecurity industry is a common language and framework to discuss and analyze the capabilities of an attacker’s TTP. Having the ATT&CK framework allows clients to better understand the behaviors of an adversary instead of analyzing the endless malware (adversary’s tools). Due to the level of sophistication in modern-day cyber attacks, the Cyber Kill Chain model alone is incapable of fully capturing and narrating an attack. The MITRE ATT&CK framework documents and catalogs adversarial behavior over 330 attack techniques broken down into 12 different categories. In joining the latest round of MITRE ATT&CK evaluations, CyCraft seek to tell the world that we are ready to defend against modern-day threats and attacks — even APT29.
But who is APT29?
The General Intelligence and Security Service (the intelligence and security agency of the Netherlands or AVID) believes APT29 to be led by the Russian Foreign Intelligence Service e.g. SVR. Since as early as 2010, APT29 has been compromising diplomatic organizations and governments in Germany, South Korea, Uzbekistan, Norway, and the United States. In June 2016, APT29 (along with APT28/Fancy Bear) was implicated in the 2016 Democratic National Committee cyber attacks. Their known methods include well-planned spearphishing campaigns, commitment to stealth, long-term espionage, smash-and-grab, and customized malware. In 2014, they were able to compromise a Washington, D.C.-based company by dumping malicious executables embedded in a flash video of Office Monkeys via an email spearphishing campaign.
Due to the international notoriety of the group and its behavioral differences between APT3/Gothic Panda (the round one emulation), MITRE has selected APT29 to evaluate detection vendors for round two of the ATT&CK evaluations.
“While APT3 has focused on noisier, process-level techniques—relying on pre-installed system tools that hide malicious activity within legitimate processes—APT29 offers the chance to measure against an adversary that uses more sophisticated implementations of techniques through custom malware and alternate execution methods”
-Frank Duff, Lead Engineer of the MITRE ATT&CK Evaluations
The tools of the twenty-one vendors will be evaluated on their ability to deal with a seasoned actor of varying sophisticated and subtle attack patterns. Will the tools be capable of detecting not only well-known TTP but also be thorough enough to detect lesser-known TTP?
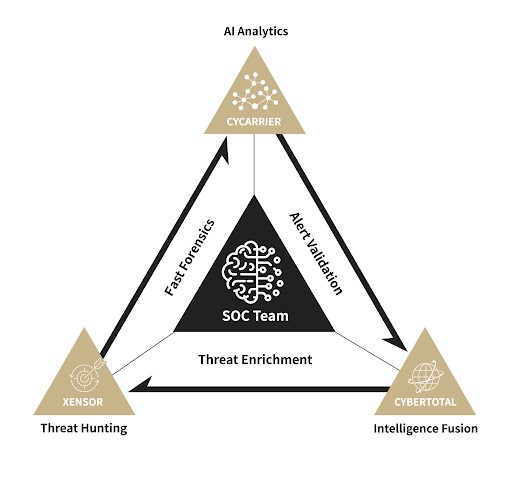
CyCraft offers a full MDR solution through endpoint protection, AI-driven investigation, and accumulated global threat intelligence. Delivered by our CyCarrier AIR platform, which includes Xensor, CyCarrier, and CyberTotal, our MDR can go from detection through validation all the way to remediation in under 60 minutes.

We are thankful that a trusted organization like MITRE exists to emulate very true-to-life sophisticated APT attacks to test products and services. We are confident that the MITRE ATT&CK Round Two evaluations will reveal positive results. CyCraft won’t let Cozy Bear maul you — not even a scratch.