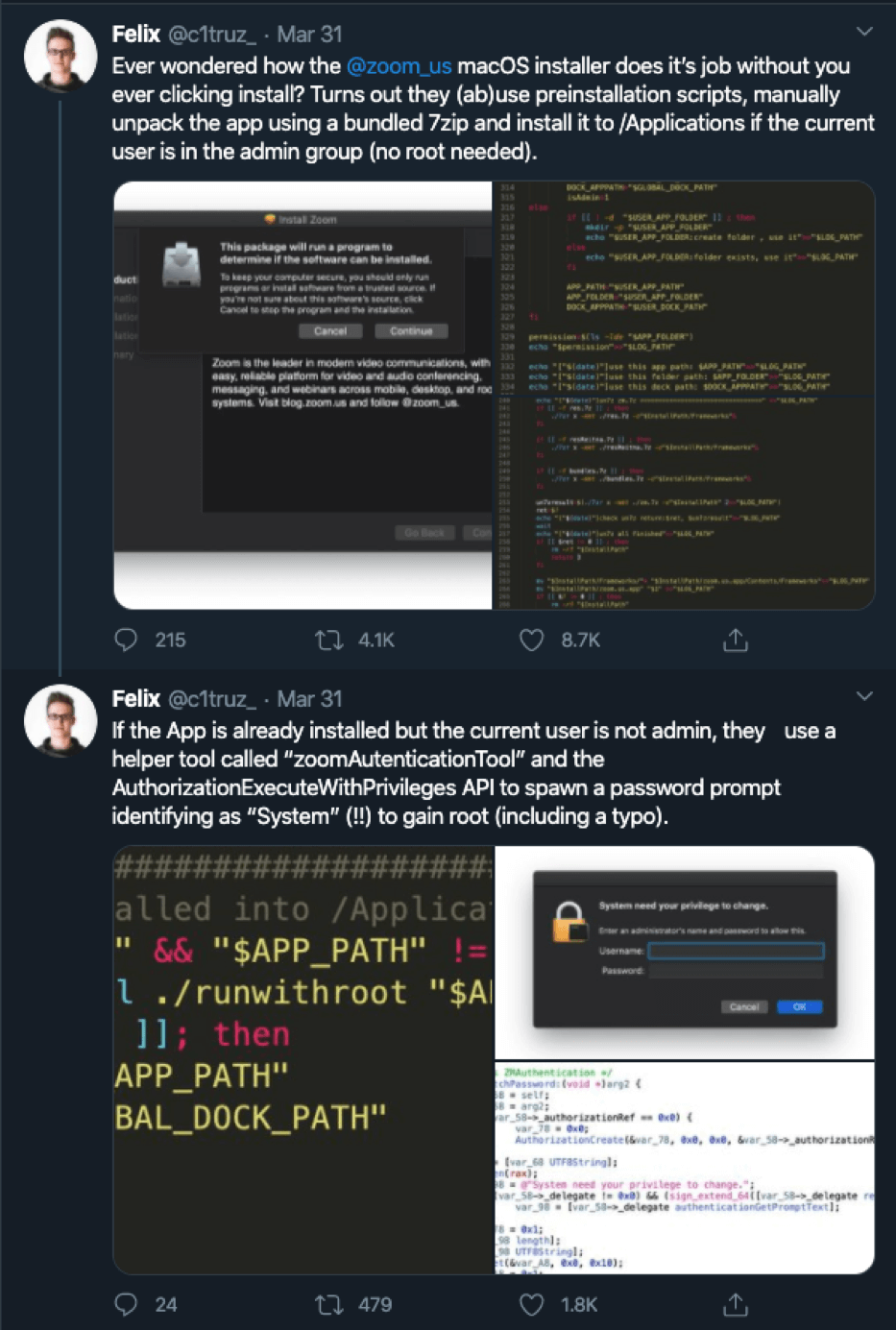
The COVID-19 pandemic has led to a worldwide work-from-home experiment spiking the sales of laptops and videoconferencing software around the world. Zoom’s UI-focused design goal to remove user friction in videoconferencing allowed Zoom.us to become the 6th most used site in America and the 18th most used site globally, Alexa reports.
Admittedly, Zoom is easy to set up, easy to use, and lets up to 100 people join a meeting for free. It just works, but for whom?
Just as quickly as Zoom’s user base increased in size, cybersecurity experts and users across the world revealed multiple serious security gaps and vulnerabilities. Most notable are the concerns in Zoom’s infrastructure, specifically the transmission of meeting encryption keys through China.
Due to these security vulnerabilities causing a severe backlash from the community, Zoom has been diligent about fixing all reported vulnerabilities, as demonstrated by their release of Zoom 5.0 on April 27th. However, as security-focused investigative journalist Kim Zetter tweeted on April 2nd, it’s “too bad they didn’t save themselves some grief and engage in some security assessments of their own to avoid this trial by fire.”
Based on our research, we assess that Zoom’s software development is still in a stage of rapid development–its trial by fire. Although most vulnerabilities have been fixed, this trial by fire clearly shows that Zoom is still developing its platform and security practices. Vulnerabilities are still prone to occur.