Security Consulting Services

Manpower – Processes – Technology
24×7 Managed Security Services

AI-enabled Threat Center
Next-Gen Security Operations Center (SOC)

AI-driven Detection, Analysis and Reports
Challenges | Lack of Automation
Challenges (brief intro)
Challenges | Cluttered Tools

Challenges (brief intro)
Challenges | Costs

Challenges (brief intro)
Challenges | Cybersecurity is Complex
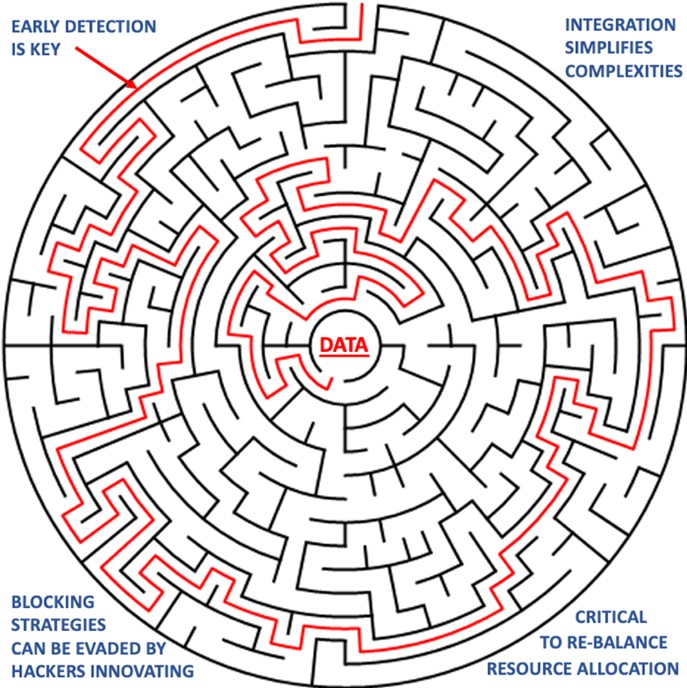
Challenges (brief intro)
Part 6: Fuchikoma ML v3
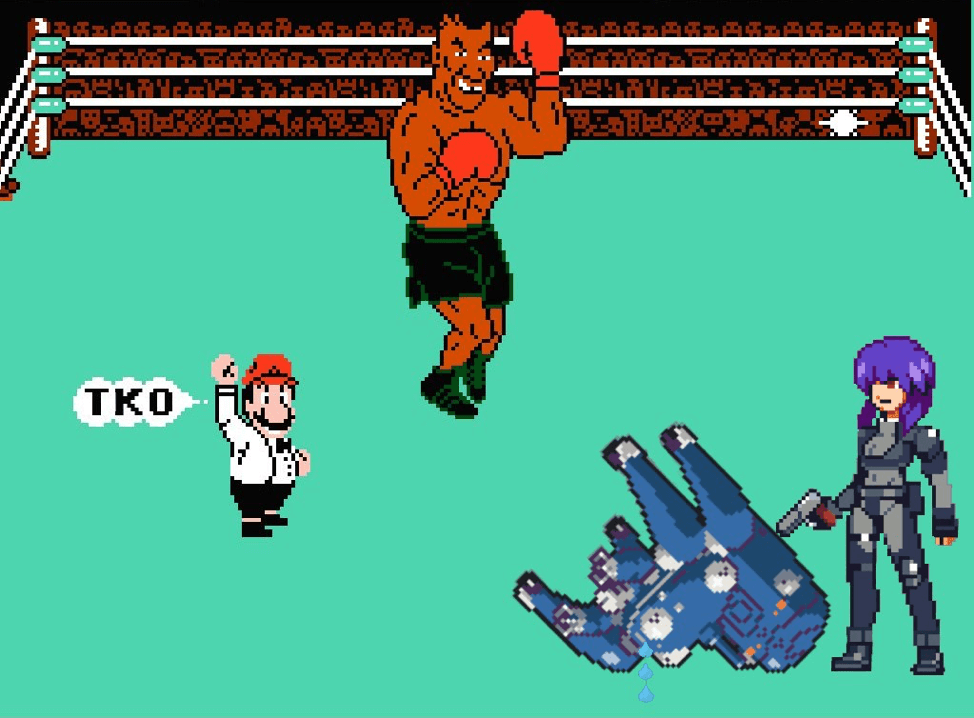
How to Train a Machine Learning Model to Defeat APT Cyber Attacks Part 6: Fuchikoma v3: Dodge, Counterpunch, Uppercut! This is Part 6 in a multi-part series of articles about how CyCraft Senior Researcher C.K. Chen and team step-by-step used open-source software to successfully design a working threat hunting machine learning model. We suggest starting […]
Part 5: Fuchikoma v2

How to Train a Machine Learning Model to Defeat APT Cyber Attacks Part 5: Fuchikoma v2 – Jab, Cross, Hook, Perfecting the 1-2-3 Combo This is Part 5 in a multi-part series of articles about how CyCraft Senior Researcher C.K. Chen and team step-by-step used open-source software to successfully design a working threat hunting machine […]
Part 4: Fuchikoma v1
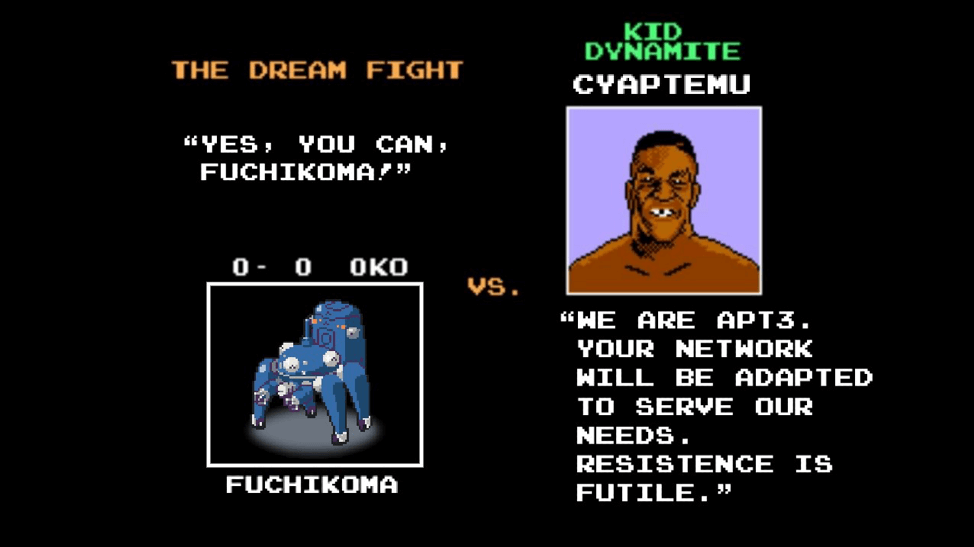
How to Train a Machine Learning Model to Defeat APT Cyber Attacks Part 4: Fuchikoma v1 – Finding the Fancy Footwork This is Part 4 in a multi-part series of articles about how Cybots Senior Researcher C.K. Chen and team step-by-step used open source software to successfully design a working threat hunting machine learning model. […]