RISK INTELLIGENCE
How do you gain visibility into the dark web, see exactly what adversaries have on you, and build an effective defense?
Request for your RiskINT Report Today

How do you gain visibility into the dark web, see exactly what adversaries have on you, and build an effective defense?
Request for your RiskINT Report Today
Your brand, your customers, your accounts, your data, and your infrastructure are all at risk in today’s cybersecurity ecosystem. You and your partners’ sensitive data resides on the deep, dark, and even surface web.
Every day, adversaries are buying and selling intelligence on potential targets: accounts, passwords, documents, spreadsheets, emails, as well as other data and communications.
After that, it’s only a matter of time before your intel is leveraged against you in order to infiltrate your organization, exploit it, disrupt it, and exfiltrate even more sensitive data. Risk no longer exists solely within your digital environment but beyond your firewall as well.
Gain sight beyond sight. Risk Intelligence (RiskINT) enhances proactive defense capabilities, giving you the time necessary to prepare an effective defense to better protect your brand, intellectual property, and technology infrastructure.
Gain granular visibility into your leaked accounts, passwords, documents located on the dark web, and
phishing domains targeting your enterprise.
RiskINT is a granularly detailed report covering:
See which of your domains and accounts are for sale on the dark web, including usernames, passwords, and cookies.
See what sensitive documents have been leaked into the wild, including purchase order forms, product specs, and employee personal information.
See credential leaks from third-party services, including usernames, passwords, and hashed passwords
See risky phishing domains, which have names similar to your branding—triaged by projected severity of impact from our global threat intelligence surveillance platform.
WHERE CAN YOUR DATA BE FOUND?
Cybercriminals do not always ask the organisation they stole from for ransom. They may simply sell it on the dark web, or even disguise themselves as your organisation.
We can analyse activities on the dark web for leaked data, stolen credentials, and phishing websites for our clients.
SURFACE WEB (4%)
DEEP WEB (95%)
DARK WEB (1%)
In addition to leveraging valid accounts and leaked documents for initial access, adversaries also phish, leading to business email compromise (BEC). Phishing can come in the form of websites used to spread disinformation and damage your brand’s reputation.
RiskINT Pro defends against this by providing proactive phishing intelligence. Know what domains to look out for, which ones mimic your domains, and which ones are malicious.
Attackers use phishing emails and compromised accounts to break in often with the purpose of obtaining sensitive information. But in many cases, that information is already available on the deep and dark web. RiskINT Premium takes you behind the scenes to show you what is already out there for sale, allowing you to take action and prevent further damage.
RiskINT Pro defends against this by providing proactive phishing intelligence. Know what domains to look out for, which ones mimic your domains, and which ones are malicious.
Our Threat Intel should be the first and last line of defense for any network seeking resilience against modern threats.


You will receive an eradication plan with complete site-wide hacker tools and behaviour analysis within 1 day of our scanner runs. This is facilitated by the seamless collaboration between our expert analysts, our virtual forensic analyst AI and attacker-behaviour modelling technology.


We provide automated forensic analysis across multiple levels of context that includes the intricate relationships between each of those levels of context.


Our Incident Response services team walks you through fully-actionable eradication plans, explaining each step simply and clearly.


We rescan and confirm eradication with cyber threat intel from multiple major proprietary sources, organizations across the globe and through our rigorous AI-driven vetting process.


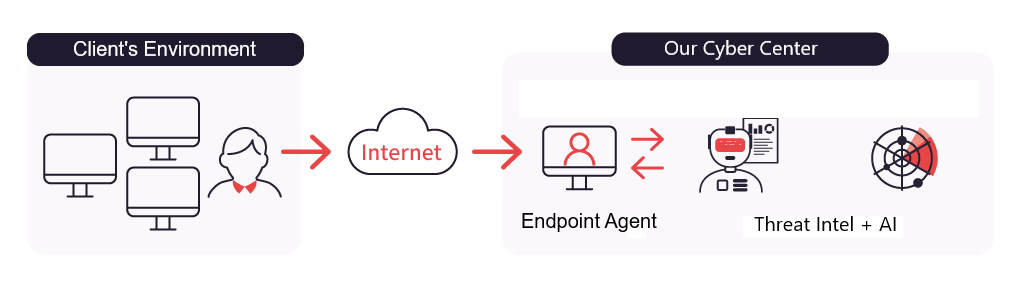
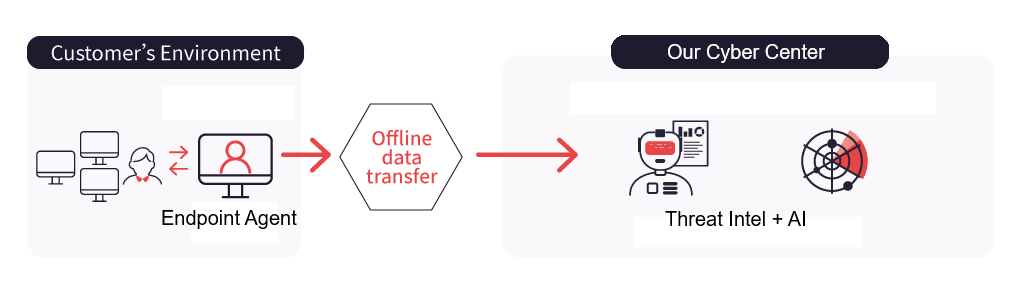
Deploy our incident response and forensic scanner to your endpoints.


We receive the scanner data & our AI & experts analyze it.


We generate a plan & execute it with you.


Together we rescan & confirm eradication.


We provide you with clear, concise and fully actionable reports covering everything you need to know to get back to healthy status.


Full storylines of any & all malicious activity


Malicious domain, IP and URL analysis


Malware analysis


A step-by-step plan for eradication


MITRE ATT&CK mapping


True system-wide root cause analysis


Graphs of all affected nodes and executions


Eradication confirmation

Up-to-date Global Cyber Threat Intelligence
Consult our cybersecurity experts today!
By submitting my contact information, I consent to the processing of my data by Cybots and its partners. I acknowledge that information submitted may be used by and associated with other information Cybots has collected and used pursuant to its Privacy Policy
The Cybots team is here to be your cybersecurity partner. Whether it’s the Initial Assessment, Managed Services or Cybersecurity Products.
If you need immediate assistance for a possible breach, please fill in the contact form.
Alternatively you can contact us at
Tel: +65 69835690 or,
Email: contactus@cybotsai.com
and a Cybots consultant will assist you with your request.
© Copyright – 2023 Cybots | All rights reserved.