What is RansomExx?
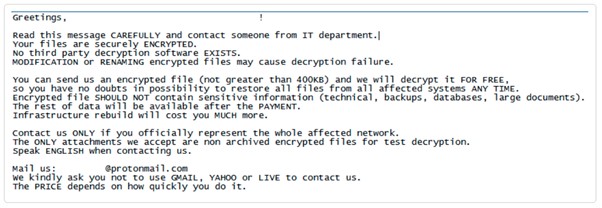
RansomExx is notorious as one of the newest ransomware groups that continue to implement cyberattacks across the world. The RansomExx ransomware gang has been in operation since 2018 but came into prominence in 2020 after infecting a variety of high-profile organizations
An Introduction To MITRE ATT&CK

The MITRE Corporation, a not-for-profit org that manages FFRDCs, released the ATT&CK Framework in 2015. ATT&CK is a living, growing framework of common tactics, techniques, and procedures (TTP) used by advanced persistent threats (APTs) and other cybercriminals.
Prometheus Ransomware Decryptor

How To Partially Recover Your Encrypted Files.
What is Lemon Duck Attack?

The objective of Lemon Duck is to steal credentials, remove security controls in an organization, spread through the organization via email and allow threat actor moves within the network without a trace.
What is Kaseya attack?
Kaseya VSA is a cloud-based MSP platform that allows providers to perform patch management and monitoring for the customers.
CVE-2021-1675 (CVE-2021-34527) PrintNightmare
This vulnerability is also known as PrintNightmare and the Print Spooler Bug. Microsoft also recently renamed this new vulnerability CVE-2021-34527. The original CVE-2021- 1675 was patched due to allowing an EoP hole; however, further issues were brought to light that CVE-2021- 1675 could also be used for RCE. This is the vulnerability to which we are referring.
Part 6: Fuchikoma ML v3
How to Train a Machine Learning Model to Defeat APT Cyber Attacks Part 6: Fuchikoma v3: Dodge, Counterpunch, Uppercut! This is Part 6 in a multi-part series of articles about how CyCraft Senior Researcher C.K. Chen and team step-by-step used open-source software to successfully design a working threat hunting machine learning model. We suggest starting […]
Part 5: Fuchikoma v2

How to Train a Machine Learning Model to Defeat APT Cyber Attacks Part 5: Fuchikoma v2 – Jab, Cross, Hook, Perfecting the 1-2-3 Combo This is Part 5 in a multi-part series of articles about how CyCraft Senior Researcher C.K. Chen and team step-by-step used open-source software to successfully design a working threat hunting machine […]
Part 4: Fuchikoma v1
How to Train a Machine Learning Model to Defeat APT Cyber Attacks Part 4: Fuchikoma v1 – Finding the Fancy Footwork This is Part 4 in a multi-part series of articles about how Cybots Senior Researcher C.K. Chen and team step-by-step used open source software to successfully design a working threat hunting machine learning model. […]
Part 3: Fuchikoma v0
How to Train a Machine Learning Model to Defeat APT Cyber Attacks Part 3: Fuchikoma v0 – Learning the Sweet Science Fuchikoma ML model training for its big fight against CyAPTEmu, the APT Emulation This is Part 3 in a multi-part series of articles about how Cybots Senior Researcher C.K. Chen and team step-by-step used open […]