What is RansomExx?
Executive Summary
This document describes the recent Cyber Attacks on StarHub and Gigabyte servers. The attack exploited vulnerabilities in a Gigabyte server. It impacted approximately 800 businesses using Starhub/Gigabyte equipment and 1,500 businesses using Gigabyte equipment worldwide. PC component maker Gigabyte and Singapore Telco StarHub were compromised in an attack targeting several of their internal servers. This attack uses ransomware at the company’s internal servers instead of the system. According to Starhub, there were more than 57,000 StarHub customers that were exposed in this breach and this data was “illegally uploaded” to a third-party data dump website.
Current Exploit Strategy
Based on the investigation by StarHub, the internal cybersecurity team discovered a third-party data dump website (C2C) and an illegally uploaded file containing limited types of customers personal information related to certain individual customers. The personal data appears to be around 14 years old. The data files comprise identity card numbers, mobile numbers, and email addresses belonging to 57,191 individual customers who had subscribed to StarHub services before 2007.
According to StarHub, there is no credit card or bank account information at risk and no StarHub information systems or customers’ database were compromised. There is no current indication that any data in this breach has been maliciously misused.
The threat actor used the following methodology to compromise the system:
- Hardware component vulnerability – used gateway to breach the system with malicious code.
- Unpatched devices – exploits the system with code execution and stays hidden in the environment.
- Privileged access level – Once the threat actor lurks in the network, they can elevate their permission level to connect with third party applications or websites.
- Payload execution – Once the threat actor gains access, they will be able to inject payloads into vulnerable devices to compromise and mine data.
RansomExx
RansomExx is notorious as one of the newest ransomware groups that continue to implement cyberattacks across the world. The RansomExx ransomware gang has been in operation since 2018 but came into prominence in 2020 after infecting a variety of high-profile organizations which include Gigabyte and Starhub.
- Targeted attack: RansomExx is used as a part of multi-stage ‘human-operated’ attacks targeting various organizations. It is delivered as a secondary payload after an initial compromise of the targeted network.
- Security products Terminated: RansomExx is capable in disabling various security products for smooth execution on the infected machines.
- Multi-Platform: RansomExx was mainly found to infect Windows systems, but current studies show this malware infects Linux systems as well by sharing similarities with its predecessor.
- Fileless ransomware: This malware is usually delivered as a secondary in-memory payload without ever touching the disk. This makes it harder to detect.
RansomExx Behavior
Investigations on RansomExx focus on the Windows variant which can be classified as ‘files malware’ because it is reflectively loaded and executed in memory without touching the disk. Analysis shows the malware reveals indicative information such as the “ransome.exx” string that can be seen hard coded in the binary.
Once the malware is executed, RansomExx will decrypt necessary string information from the infected endpoints and generate the GUID of the machine.
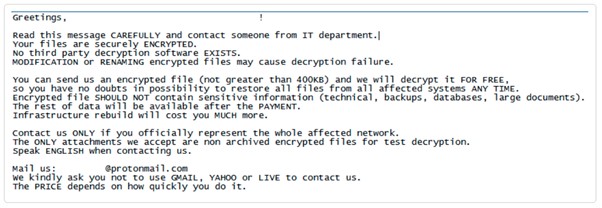
The malware will continue terminating processes and system services that may interfere with the execution such as Security agents and many more. Once RansomExx encrypts the files, they will leave the following note in the victim’s machines.
Victims of RansomExx
- Starhub Singaporean Telco
- OrangeTee
- Taiwanese motherboard maker(GigaByte)
- Italy’s Lazio region
- Ecuador’s state-run Corporacion Nacional De Telecomunicacion (CNT)
Indication of Compromise
The following are the malicious MD5 checksums. Cybersecurity teams can scan for the following files.
• AA1DDF0C8312349BE614FF43E80A262F
• B0FD45162C2219E14BDCCAB76F33946E
• CB408D45762A628872FA782109E8FCFC3A5BF456074B007DE21E9331BB3C5849
• 91AD089F5259845141DFB101
• DA3BB9669FB983AD8D2FFC01AAB9D56198BD9CEDF2CC4387F19F4604A070A9B5
• C7B28FE059E944F883058450D5C77B03076B0EA1
• 1A3D0FDDF65F7CCA188499E
• 652259F1F6393D71240D6643573C09F4
• DA0921C1E416B3734272DFA6
• 1717402591B663767B37B3CE0635D991ACE08432
Domain
This is the list of malicious domains which threat actors are using. Cybersecurity teams can add them to the list of blocked domains.
artilleryin.online | awerityubfer.club |
berxion9.online | bowepripos.uno |
caliberunity.club | vatet.sm |
trojan.win32.vatet.sm | timerework.fun |
pexxota.space | cleantheplace.top |
wellernaft.top | cleantheplace.top |
kastellira3.space | shrapnell.space |
Remediation and Mitigation Plan
- Patch operating systems, applications, and keep antivirus signatures up to date.
- Ensure the endpoints and server have different layers of security appliances.
- Cybots recommends that organizations perform Compromise Assessment (CA) as an initial action to identify any anomalies and threat actor movement.
- Cybots recommends that organizations subscribe to Advanced Managed Detection & Response (AMDR) services to detect the suspicious activity in the endpoints with our AI analysis.
- Implement training and processes to identify phishing & externally-sourced emails.
- Maintain offline, encrypted backups of data and regularly perform health checks on servers.
- Advise users to implement complex password specially for Local/Domain Administrator. This needs to be changed on regular basis.
- Ensure that the endpoint is patched with the following CVE’s (CVE-2019-1338, CVE-2018-13379, CVE-2019-5544, CVE-2020-3992, CVE-2021-1732, CVE-2020-1472)