In cybersecurity, there have been several approaches used to track and analyze the various characteristics of cyber intrusions by advanced threat actors.
Two Seminal Approaches to Intrusion Analysis
1. Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains
In 2011, the US Department of Defense officially incorporated cyberspace as a component of the fifth domain of warfare, Information Operations; the first four consisting of land, sea, air, and space.
The defense contractor, Lockheed Martin, extended the military concept of a kill chain and adapted it to cybersecurity. The Cyber Kill Chain, as it is currently called, breaks down an intrusion into a well-defined sequence of seven phases from Reconnaissance to Actions on Objectives.
2. The Diamond Model of Intrusion Analysis
In 2013, the US Department of Defense released its model for intrusion analysis. The Diamond Model emphasizes the relationships and characteristics of an intrusion’s four core features: adversary, infrastructure, capability, and victim.
It further defines additional meta-features to support higher-level constructs and applies measurement, testability, and repeatability to provide a more comprehensive scientific method of analysis.
The Modern Lexicon
MITRE ATT&CK™: Design and Philosophy
While the Diamond Model and the Cyber Kill Chain are still used and referenced today, most cybersecurity industry professionals use the MITRE ATT&CK Framework and its terminology. Vendors use ATT&CK terminology in their solutions. Organizations use ATT&CK terminology to standardize community conversations, defense testing, and product/service evaluations.
The MITRE Corporation, a not-for-profit org that manages FFRDCs, released the ATT&CK Framework in 2015. ATT&CK is a living, growing framework of common tactics, techniques, and procedures (TTP) used by advanced persistent threats (APTs) and other cybercriminals. MITRE ATT&CK makes their matrices accessible to the private sector, governments, the cybersecurity product and service community, and the general public.
ATT&CK has been rapidly adopted by the community because, unlike the Diamond Model or Cyber Kill Chain, ATT&CK maps and indexes virtually everything regarding an intrusion from both the attack and defense sides. ATT&CK includes data on threat groups, their TTPs, and even provides references and examples. Attack scenarios mapped via ATT&CK can be reproduced by red teams, and tested by blue teams. ATT&CK, due to the Evaluations, now has data on cybersecurity vendors, their solutions, and their capabilities. None of these can be done with either the Diamond Model or the CKC.

ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. The framework is a matrix of intrusion techniques sorted into 12 different tactics.
As of March 2020, ATT&CK currently has four main matrices: PRE-ATT&CK, Enterprise, Mobile, and its most recent addition, ICS. The Enterprise ATT&CK matrix, the most commonly referenced matrix, combines four separate matrices: Windows, macOS, Linux, and Cloud.
Since its release in 2015, ATT&CK has become one of the most referenced and most respected resources in cybersecurity. The Enterprise ATT&CK matrix currently lists 226 unique adversarial techniques alphabetically from the shell scripts .bash_profile and .bashrc to XSL Script Processing.
The Seven Phases of the Cyber Kill Chain
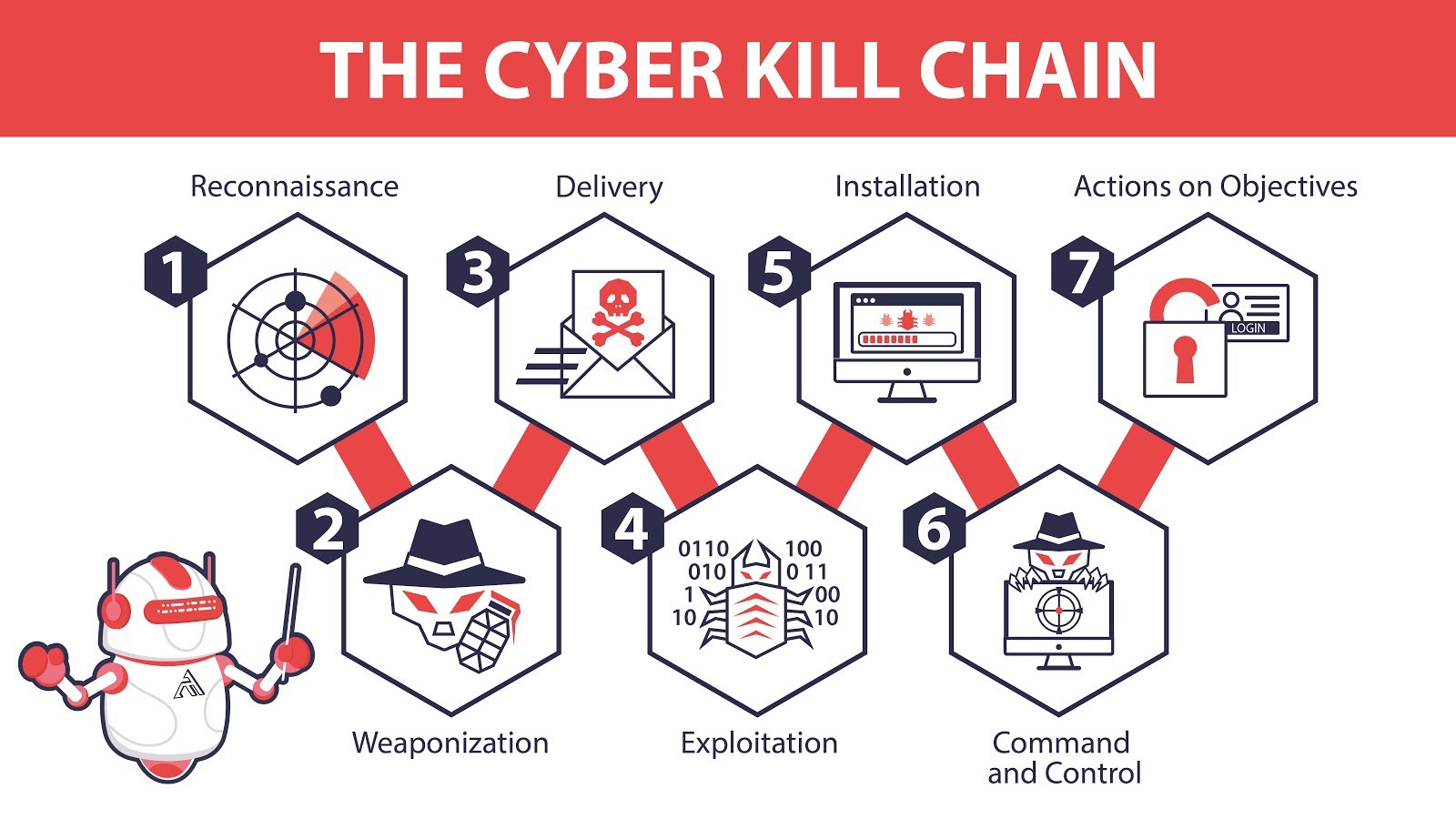

Cyber Kill Chain and MITRE ATT&CK both follow the typical narrative of an attack — for example, break in, be stealthy, steal some data. However, while the Cyber Kill Chain has a clearly defined linear sequence of phases, the ATT&CK Framework is a matrix of intrusion techniques that is not confined to a specific order of operations.
The Cyber Kill Chain applies the century-old military kill chain model to a cyberattack. It’s designed for defenders to improve their defenses by analyzing an attacker’s playbook (the kill chain) and interrupting the attack by breaking the kill chain at each phase.
- Reconnaissance — Attackers gather information about their target. This includes indirect and passive methods where attackers gather information from public resources such as ARIN (American Registry for Internet Numbers) registrations, Shodan, or job listings. Then attackers will shift to more direct and active methods such as port scanning.
- Weaponization — Attackers now create an attack that exploits vulnerabilities found in reconnaissance; many leverage tools from metasploit, exploit-db, or a social engineering toolkit.
- Delivery — Once an attacker has chosen which tools are best suited to exploit your vulnerabilities, they will select their delivery method, be it phishing emails, infected USBs, or another method of choice.
- Exploitation — The weapon has been delivered. The attacker just needs to execute the attack, which could take the form of a SQL injection, a buffer overflow, RCE, as well as countless others.
- Installation — The attacker gains better access. Common adversarial techniques include executing powershell in fileless attacks, installing remote access tools (RAT), and DLL hijacking.
- Command & Control (C2) — The attacker now sets up persistent access to your system for remote manipulation. Depending on their end goals, the attacker could act immediately or lurk in your system from months to years. Access could persist even after rebooting or patching the initial vulnerability and is often encrypted and masked to look like normal traffic. Sometimes, it’s even embedded within normal legitimate traffic, such as Twitter or email.
- Actions on Objectives — The attacker achieves their intrusion objective, e.g., data exfiltration, data destruction, or denial of service.
The Cyber Kill Chain is more than a model for an attack. The seven phases of the Cyber Kill Chain provide an excellent foundation for any organization’s security design. However, as the old saying in cybersecurity goes, “Defenders need to defend against everything while attackers only need to exploit one weakness.”
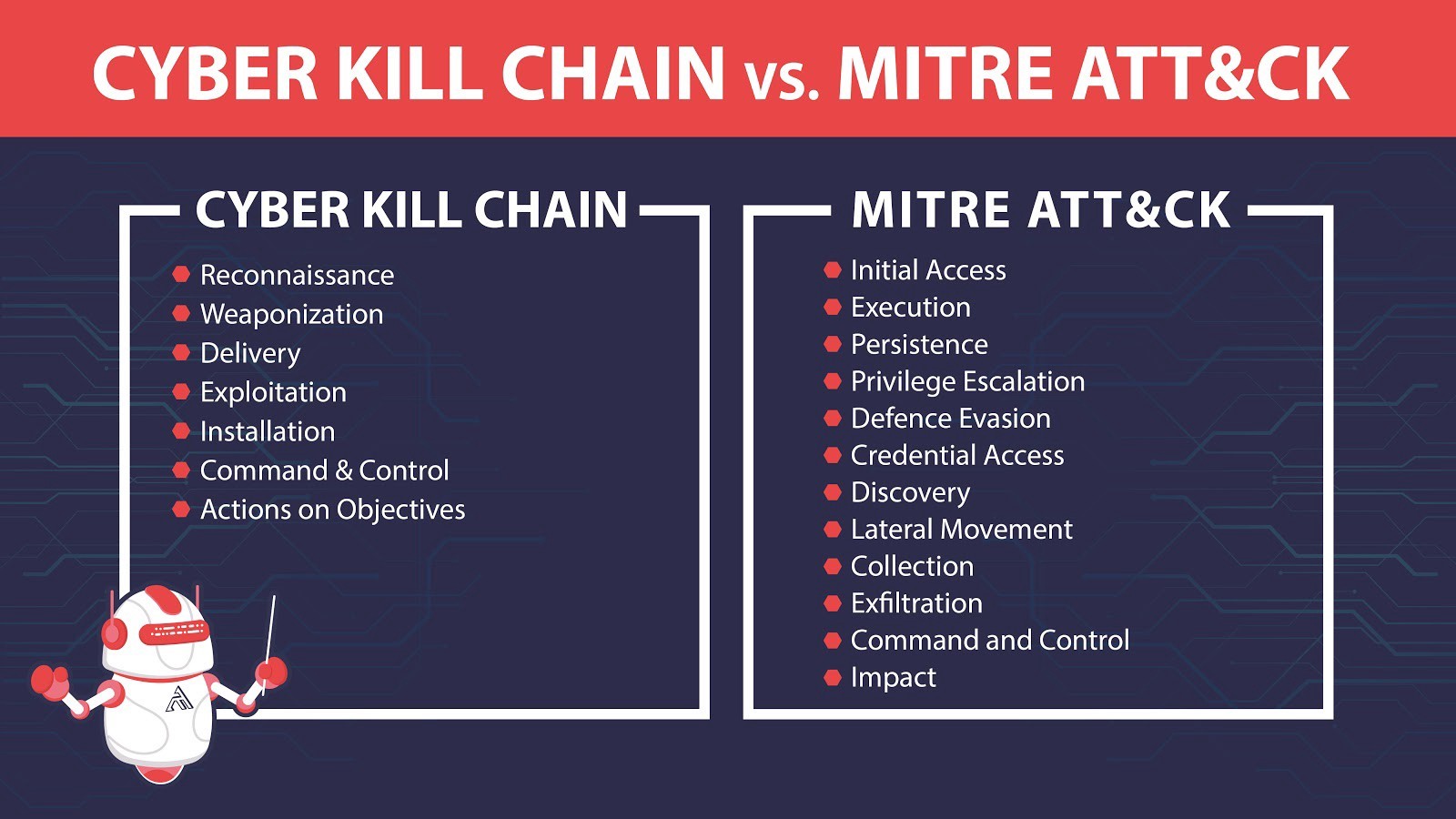
Cyber Kill Chain vs. MITRE ATT&CK

Most security analysts will tell you that in the current cybersecurity landscape, intrusions are no longer a question of if, but of when. Attackers will get into your system eventually. This is why organizations have been gradually expanding beyond their prevention systems to detection and response solutions.
In some ways, the MITRE ATT&CK Framework is a response to this shift of resources. Unlike the theoretical Cyber Kill Chain model, the ATT&CK Framework is directly based on the research from millions of real-world attacks.
The Enterprise ATT&CK Matrix expands elements of the Cyber Kill Chain into 12 categories called Tactics, which are then further expanded granularly into specific known adversarial Techniques. Inside of each Technique is a listing of research highlighting specific Procedures for how a threat actor executed that given Technique.
It is important to note that there is not a one-to-one mapping with the Cyber Kill Chain, but that these tactics, techniques, and procedures can be used along the Cyber Kill Chain phase by phase.
Take the ATT&CK Discovery tactic, for example. Attackers could run a port scan during initial reconnaissance before they’ve gotten a foothold or midway through their attack as they are preparing to further infiltrate internal systems.
The MITRE ATT&CK Framework
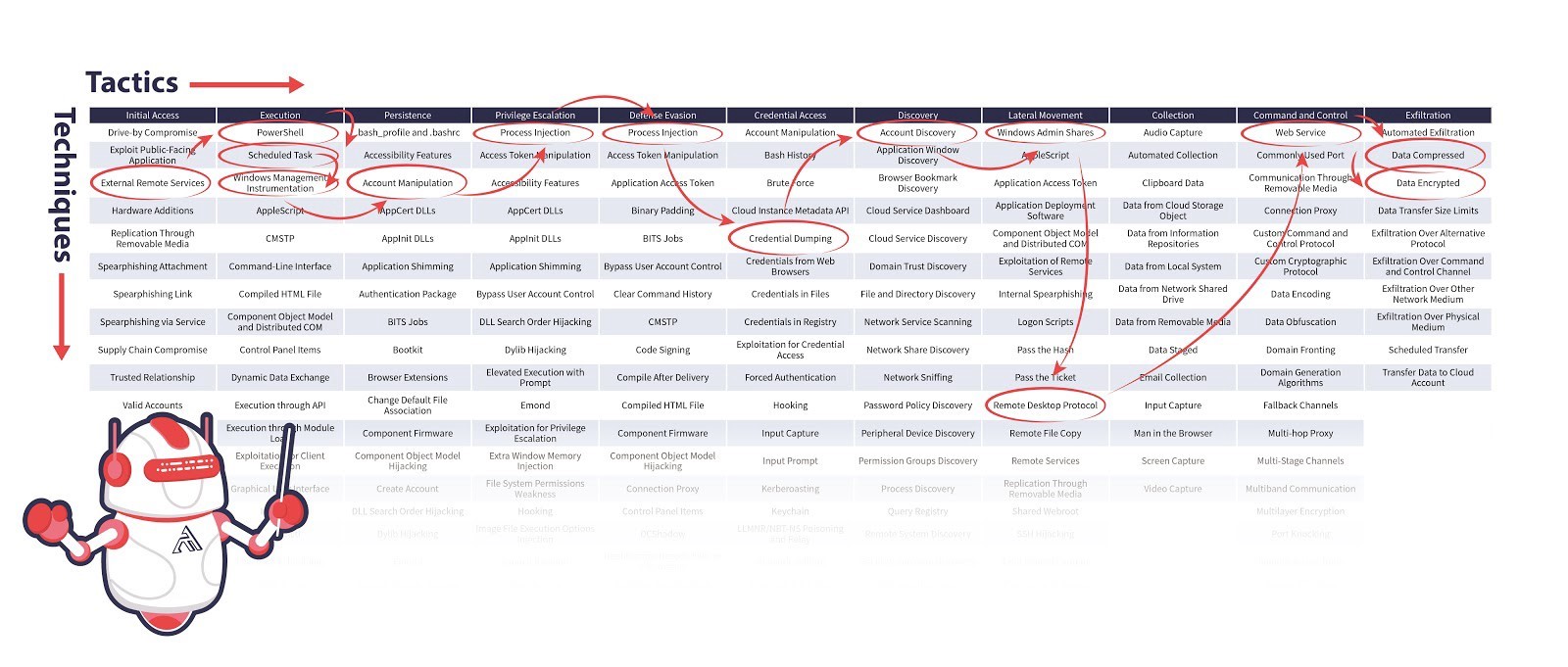

Tactics and techniques used by APT Chimera during Operation Skeleton Key
The ATT&CK Matrix is composed of tactics, techniques, and procedures, otherwise known as TTP. Following the 12 columns, or tactics, from left to right, are another take on steps an attacker would typically follow when attacking your organization.
Multiple techniques can be employed to accomplish the same tactic, and depending on the attacker’s main objective, not all 12 tactics need to be employed. The aggregate of techniques used during an attack is known as the behavior profile — the procedure the attacker followed to accomplish their ultimate goal by attacking your system.
In June 2019, Ponemon Institute and SANS reported that the mean time to detect (MTTD) a breach is 197 days. What can an attacker accomplish in the span of 6.5 months?
The ATT&CK Framework is essentially the attacker’s playbook — how they get in your system, how they move, what they do, what their end goals are, and how it impacts your system. At the time of this article’s publication, MITRE ATT&CK currently lists 12 common tactics for the Enterprise ATT&CK Matrix with a total of 226 known adversarial techniques.
- Initial Access — techniques that use various entry vectors to gain an initial foothold within a network (e.g., T1192 Spearphishing Link)
- Execution — techniques that result in running attacker-controlled code on a local or remote system (e.g., T1086 PowerShell)
- Persistence — techniques used to maintain persistent access to a system (e.g., T1037 Logon Scripts)
- Privilege Escalation — techniques used to gain higher-level privileges on a system or network (e.g., T1055 Process Injection)
- Defense Evasion — techniques used to avoid detection (e.g., T1073 DLL Side-Loading)
- Credential Access — techniques for stealing credentials such as account names and passwords (e.g., T1208 Kerberoasting)
- Discovery — techniques used to gain knowledge about the system and internal network (e.g., T1040 Network Sniffing)
- Lateral Movement — techniques used to enter and control remote systems on a network from the already compromised host (e.g., T1097 Pass the Ticket) Attackers typically have to pivot through multiple machines (usually the weakest link in the chain of machines) to ultimately reach their end objective.
- Collection — techniques used to gather information relevant to following through on the attacker’s objectives (e.g., T1056 Input Capture)
- Command & Control — techniques attackers may use to communicate with systems under their control, often disguised to look like normal HTTP traffic (e.g., T1172 Domain Fronting)
- Exfiltration — techniques used to steal data from your network (e.g., T1002 Data Compressed)
- Impact — techniques used to disrupt availability or compromise integrity by manipulating business and operational processes (e.g., T1495 Firmware Corruption) Impact, the most recently added tactic, is the result on your system after the attacker accomplishes their ultimate goal.
Each of the 220+ techniques on the ATT&CK matrix has a page that includes a brief summary of the adversarial technique, procedure examples, mitigations for detecting and defending against each of these attacks.
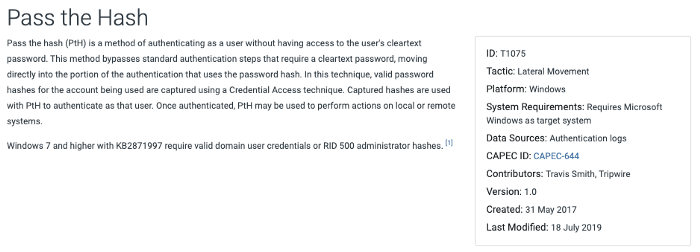

This is a screenshot of the entry for ATT&CK Technique T1075, i.e., Pass the Hash. Farther down the page, we find the known mitigations for Pass the Hash.
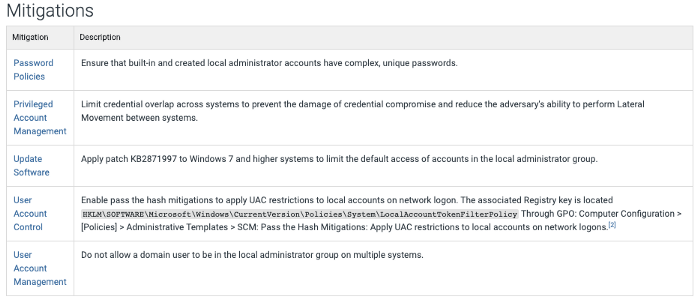

Diamond Model vs. Cyber Kill Chain
Perhaps the biggest difference between the Diamond Model and the Cyber Kill Chain is that the Cyber Kill Chain strictly follows a linear narrative approach to analyze a cyberattack. One step leads to another. The Diamond Model was designed to track a threat actor over multiple intrusions.

While the Diamond Model has a modest appearance, it can get quite complicated and in-depth quite quickly. The diamond of a threat actor is not static but is in constant flux as attackers alter their infrastructure and capabilities quite often.
Each feature of the diamond (victim, infrastructure, adversary, capability) is a pivot point that defenders can use during their investigation to connect features of one attack with others. An attack from a known zero-day attack that requires a unique deployment method would alter the capabilities of an attacker; this could be pivoted to investigate other attacks that used similar methods or the same zero-day attack.
Diamond Model vs. MITRE ATT&CK
The Diamond Model and the MITRE ATT&CK framework both add value to cyber threat intelligence but very differently.
The ATT&CK Framework is useful for understanding the behavior of threat actors via documenting the techniques, tactics, tools used in previous attacks.
As a result, defenders are therefore able to defend themselves more efficiently and accurately by understanding techniques, tactics, and tools commonly used by multiple threat actors — especially threat actors that have already attacked other organizations in their industry.
However, while the ATT&CK Framework adds value to cyber threat intelligence through the study of used tactics, techniques, and tools, the Diamond Model adds value to cyber intelligence through a deep understanding of the infrastructure and capabilities of both victim and adversary.
Attribution of a cyberattack to a threat actor is a complicated procedure that the Diamond Model excels in through all its features (both non-meta and meta). In fact, attribution should not be solely done on the analysis of an adversary’s use of TTPs alone.
Perhaps the biggest downside to the Diamond Model is that it requires a lot of maintenance. While MITRE ATT&CK is maintained directly by MITRE and indirectly by the cybersecurity community, users of the Diamond Model will need to feed it themselves.
Aspects of the Diamond Model change rapidly, especially capability and infrastructure. You could quickly end up using outdated information if you do not constantly update an attacker’s diamond.
The online living knowledge database that is the ATT&CK Framework is constantly updated, and it is made public — accessible to everyone. Chronicling attacker behavior (the techniques and tactics used in their attacks) has proven to be easily accessible and actionable to defenders. While an attacker’s infrastructure and capabilities constantly fluctuate over time, their behavior doesn’t.
The Power of Behavior
Defenders have been able to accumulate this vast amount of attacker behavior, in part, due to attackers automating their procedures; it’s how they have been able to scale upwards. Their behavior is also their Achilles Heel.
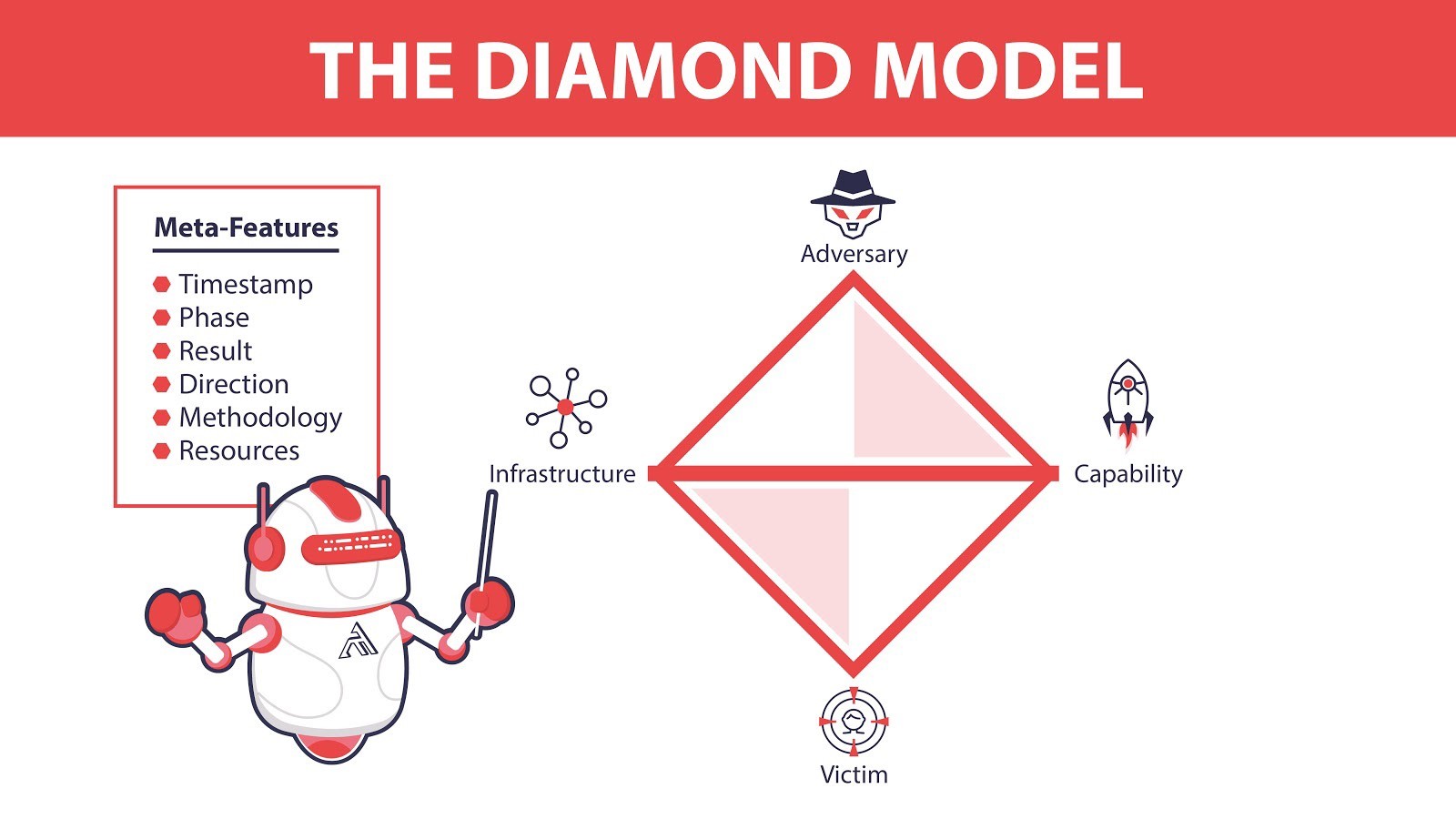
While there is no silver bullet for security safeguards that stops all attacks, knowing an attacker’s behavior is incredibly useful for defenders. The often referenced, Pyramid of Pain, illustrates this quite well. Simply put, the Pyramid of Pain shows how difficult it is for an attacker to circumvent the particular method that has been taken away from them.

For example, blocking a file or IP address is rather easy for an attacker to get around. Blocking a domain name is slightly more troublesome as the attacker might have to alter a few lines of code on their programs. Blocking FTP outbound on your network could prevent the attacker from exfiltrating data, but they could just as easily tunnel the data out through another encrypted tunnel.
Taking away an attacker’s tool is challenging as they will have to devise a new way of carrying out their objectives; however, as most security analysts will tell you programming defenses to detect tool after tool feels a bit like the game whack-a-mole. Advanced attackers often design their own custom tools or customize variations of existing tools. It takes time and is quite challenging, but it can be done by advanced attackers.
At the top of the Pyramid of Pain, are the tactics, techniques, and procedures that the ATT&CK Framework documents. This is the behavior profile mentioned earlier and is much more difficult for the attacker to alter this and circumvent defenses at this level.
Defenders could have alerts in place if Mimikatz is ever detected; however, disabling or restricting NTLM (New Technology LAN Manager) and monitoring command line arguments help defend against multiple tools used for Credential Dumping, and not just Mimikatz.
Difficulties with the Cyber Kill Chain
While the Cyber Kill Chain has been accepted in the cybersecurity community, it has not been universally adopted. Critics of the Kill Chain often point to what they believe are the fundamental flaws in the model.
- The Cyber Kill Chain assumes a traditional perimeter-focused defense where a firewall is the main line of defense and so fails to cover other attack vectors and internal attack paths; modern organizations need to leverage defensive solutions within the perimeter.
- The Cyber Kill Chain does not focus enough on what to do after an attacker has broken into your network successfully, which they inevitably can with enough persistence.
- The Cyber Kill Chain’s phase sequence cannot accurately depict all attacks as several kill chain phases can be bypassed entirely.
- Once inside a victim’s network, the timing of each attack phase is inconsistent. Phases can take anywhere from minutes to months to years. Attackers could lay dormant for prolonged periods of time waiting for the optimal window to launch the final phase of their attack to apply the most impact on their target.
Difficulties with the Diamond Model
The Diamond Model comes from a different time when there was more of a focus on analytic outcomes than process and principles — hence the opening quotation:
‘‘Intelligence analysts should be self-conscious about their reasoning process. They should think about how they make judgments and reach conclusions, not just about the judgments and conclusions themselves.”
Richards J. Heuer Jr. (ex-CIA and author of “Psychology of Intelligence Analysis”) Tweet
It was part of a push for a more intelligence-driven intrusion analysis standard, which, in many ways, is now the norm today; however, modern advancements in machine learning have propelled intrusion analysis even further through the automation of data-driven intelligence.
The Diamond Model is still useful today. While ATT&CK primarily documents adversarial behavior, the Diamond Model is more useful for clustering intrusions for analysis. These separate strengths are complementary; mapping attack techniques within the ATT&CK matrix should prove useful data for the Diamond Model when analyzing a threat actor’s capabilities.
On page 52 of the original paper, the authors (Caltagirone, Pendergast, and Betz) discussed at length on how the Diamond Model is complementary to the Cyber Kill Chain. Resources gained from one intrusion are commonly used by the attacker to enable future intrusions or exploit internal trust relationships to gain deeper access into a victim’s network. This can be displayed by combining the Diamond Model with the Cyber Kill Chain, as seen in Figure 6 below.
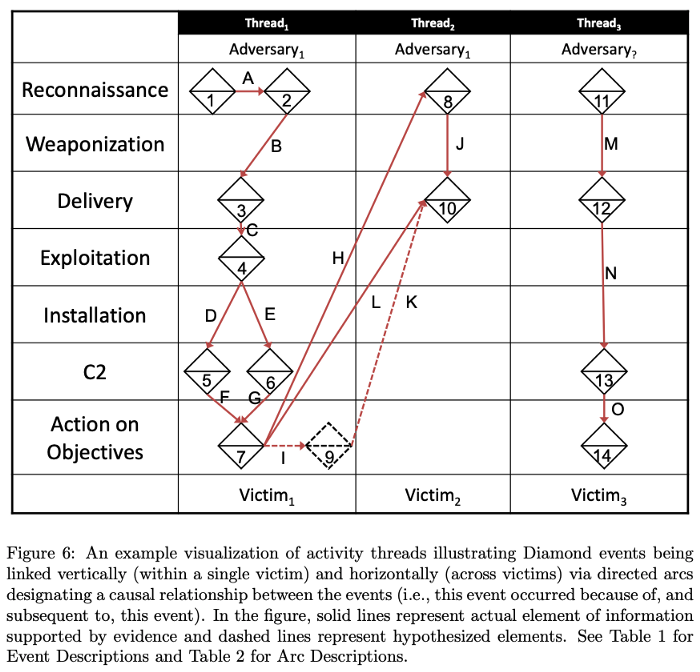

Does MITRE ATT&CK replace the Cyber Kill Chain or Diamond Models?
No.
The Cyber Kill Chain and Diamond Model are both still in use today; however, intrusion analysis is all about context. MITRE ATT&CK provides a common and precise language so defenders can have more actionable conversations backed up by easily referenceable data-driven intelligence. This modern lexicon enriches both models, which are both still useful and relevant today.
You can hear it straight from the horse’s mouth.
“ATT&CK and the Cyber Kill Chain are complementary. ATT&CK sits at a lower level of definition to describe adversary behavior than the Cyber Kill Chain. ATT&CK Tactics are unordered and may not all occur in a single intrusion because adversary tactical goals change throughout an operation, whereas the Cyber Kill Chain uses ordered phases to describe high-level adversary objectives.”
-MITRE ATT&CK FAQ Tweet
Despite MITRE ATT&CK’s claims on how ATT&CK is complementary, many researchers feel that the ATT&CK framework will (or already has) replace both the Cyber Kill Chain and Diamond Model — mostly for the reasons cited above. This is further demonstrated by the trends of vendors implementing ATT&CK terminology into their solutions and organizations requesting ATT&CK terminology in solutions.
How to Start Implementing the ATT&CK Framework into your Security
There are numerous benefits to incorporating the ATT&CK Framework into your security culture; some of which have already been mentioned, such as having actionable and data-driven conversations. Here are the five use cases for the ATT&CK Framework and the order that you should implement them into your security culture.
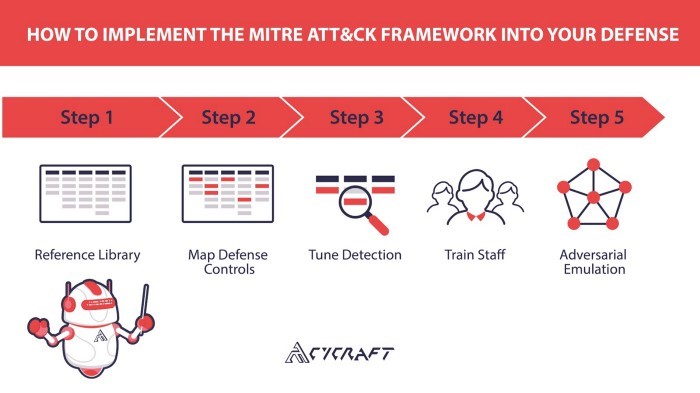

Step 1 — Reference Library
The ATT&CK Framework not only documents known adversarial techniques but also the adversaries who have used them. Don’t add to your workload. Prioritize it. The ATT&CK Framework helps your red teams and research teams focus their work with the right questions and provides leadership with a clear understanding of the security tasks ahead.
What adversaries target our specific industry? What techniques do those adversaries commonly use? What tools do those adversaries use to carry out those techniques? What’s our current coverage? Are we capable of detecting these techniques? What preventative controls mitigate this technique?
The ATT&CK Framework answers these questions and makes it easy to create heat maps of attacker techniques known to have been used against similar peers in your industry. ATT&CK Navigator on GitHub is an excellent tool for this and is quite easy to use. If you haven’t seen MITRE’s instructional video, you should. It covers most of the basic features.


In this example, we focus on threat actors who target financial institutions. Red techniques are used by all four threat actors, whereas green techniques are only used by some. White techniques have not been known to be used by these four threat actors.
ATT&CK Navigator can be used to create interactive heat maps like the one above. This particular heat map is of known techniques used by Carbanak, Cobalt Group, APT38, and FIN7 — threat actors known for targeting financial institutions.
Step 2 — Map Defense Controls
Knowing how you will be attacked is as important as knowing your own defense capabilities. Mapping your defense controls on the ATT&CK matrix will not only give a clear view of what you can defend against but is also the first step in tuning your detection and response capabilities.
Step 3 — Tune Detection
SOCs need to shift the conversation from “what we have” to “what we should have”. A common misconception by vendors of the ATT&CK Framework is that they need to check every box in the matrix. The ATT&CK Framework is not Pokemon; you can’t catch them all.
Instead of exhausting organizational resources on defending against the 220+ techniques, focus on the techniques known to have attacked similar peers in your industry.
Overlaying your controls and the known threats of your industry allows you to fill the gaps in your defense and reduce redundancies.
Step 4 — Train Staff
Train your staff on the MITRE ATT&CK Framework by implementing the tactics and techniques into your workflow and daily routines. The ATT&CK matrix itself won’t change hacker behavior, but it will and has changed the global cybersecurity conversation by creating common classifications resulting in more data-driven and actionable discussions.
Changing company culture is not easy. However, every SOC should make the shift from a compliance-based culture (worrying about audits and regulations) to a more intelligence-driven culture and prioritizing resources on the most likely threats.
ATT&CK has quickly become one of the most definitive resources of hacker techniques available today. The cybersecurity community increasingly talks about cyberattack techniques in ATT&CK terms and choosing software based on the MITRE ATT&CK Framework. Having everyone on your team familiar with the terms of the ATT&CK Framework is paramount prior to undertaking the next step.
Step 5 — Adversarial Emulation
Is your current coverage capable of detecting techniques used by adversaries that target your industry?
In July 2019, the Ponemon Institute reported that 53 percent of IT leaders don’t know if their cybersecurity controls are working. Knowing your defense capabilities is not as valuable as knowing their efficacy.
Ultimately, the best use case for the ATT&CK Framework is to test defensive solutions and provide metrics to gauge the efficacy of your defenses. This is best demonstrated through attack simulations. Many organizations do have internal red teams, and there are third party red team services out there. However, MITRE has also provided an open-source tool on GitHub called Caldera.
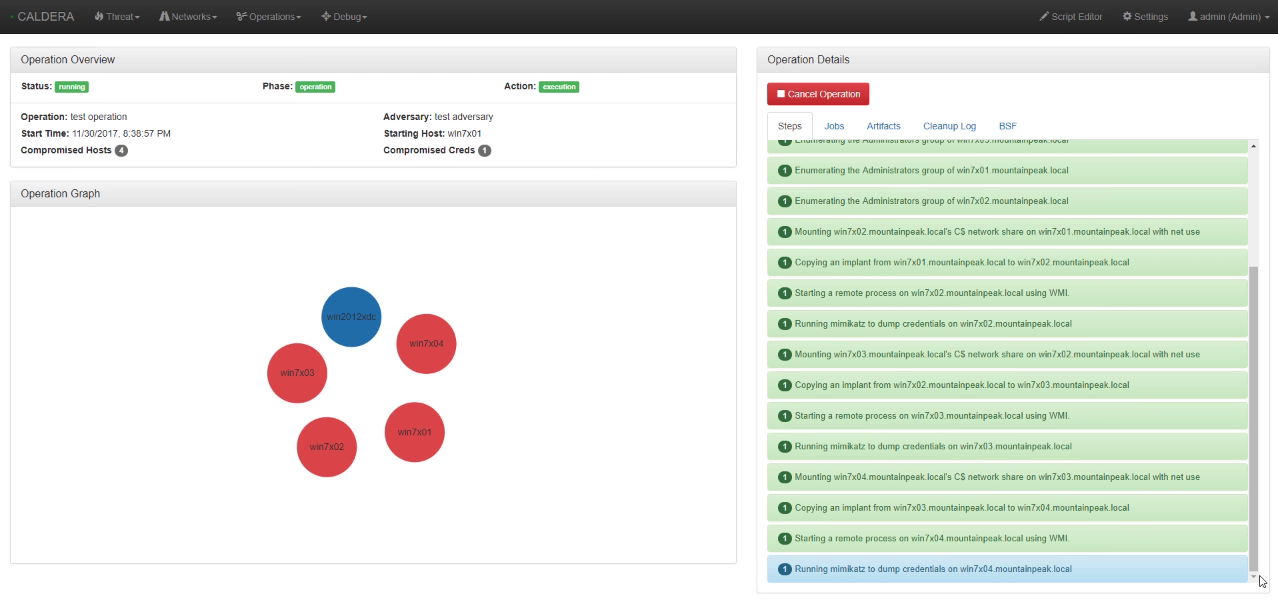

Watch MITRE’s online tutorial on Caldera here.
Caldera automates and tests systems against selected techniques in the ATT&CK Matrix. You begin by installing Caldera on your network. Then install service agents on your network that you would like to test. Your attack can be customized and configured through the Caldera GUI.
After the test runs, Caldera will go through the selected techniques and even compromise other systems it finds through the enumeration phase. It goes without saying, but users should be careful with all automated testing as it can be dangerous. If you are interested in knowing more about Caldera, read MITRE’s online introduction.
MITRE ATT&CK Evaluations
In 2018, MITRE launched the MITRE ATT&CK Evaluations, where MITRE evaluates the efficacy of cybersecurity products using an open methodology based on the ATT&CK Framework. The ATT&CK Evaluations not only provides transparency to the true efficacy of security products but also drives security vendors to enhance their defensive capabilities towards known adversarial behaviors.
While there is not a “winner” of the evaluations, nor are scores or rankings given, that has not stopped many of the leading cybersecurity vendors from participating.
The results of the 2018 ATT&CK Evaluations (round one) have already been released. Cybersecurity vendors went up against MITRE ATT&CK’s emulation of APT3 — a China-based threat group that researchers have attributed to China’s Ministry of State Security.
While only 12 vendors joined the 2018 Evaluations, 21 vendors participated in the 2019 ATT&CK Evaluations, where defenders went up against an emulation of APT29 — a threat group that has been attributed to the Russian government.
Results of the second round of MITRE ATT&CK Evaluations should be released by 2020 Q2. CyCraft became the first cybersecurity firm from Taiwan (and second from Asia) to participate in the MITRE Evaluations. Read about the CyCraft approach against the APT29 attack simulation.
MITRE has already announced the emulation for the 2020 ATT&CK Evaluations. Vendors will be defending against the threat groups Carbanak and FIN7 — threat groups known for targeting financial institutions. CyCraft will be there again.


As of 2020, MITRE Engenuity, an independent nonprofit organization, will be managing the oversight of the MITRE ATT&CK Evaluations program.
MITRE ATT&CK Evaluations
- Round One — APT3, Results released in November 2018.
- Round Two — APT29, Results released in April 2020.
- Round Three — Carbanak + FIN7, Registration in progress.
MITRE ATT&CK Today
Unfortunately, there was more than one Matrix movie. (Sorry, Neo.) Fortunately for us, there is now more than one ATT&CK Matrix.
Since its release in 2015, ATT&CK has expanded beyond the original Enterprise Matrix. The ATT&CK Framework now includes matrices for Mobile (for both iOS and Android), PRE-ATT&CK, and ICS (Industrial Control Systems). The living knowledge base has grown considerably.
MITRE makes regular updates to ATT&CK. Follow their blog to stay up-to-date with the latest developments.
In addition to Caldera and ATT&CK Navigator, MITRE also offers an open-source blue team toolset called Cascade.
MITRE has also launched the Cyber Analytics Repository. The repository is a separate project from ATT&CK and is an open analytic collaboration project with detailed information on how to detect ATT&CK techniques.
Most recently, MITRE has launched a software certification process. Software companies can become certified by MITRE based on their ability to detect ATT&CK techniques.
Everything Starts From Security
Prevent cyber intrusions from escalating into business-altering incidents. From endpoint to network, from investigation to blocking, from in-house to cloud, Cybots covers all aspects required to provide small, medium, and large organizations with the proactive, intelligent, and adaptable security solutions needed to defend from all manner of modern security threats with real-time protection and visibility across the organization.