The Desorden group claims to have stolen over 400GB of files
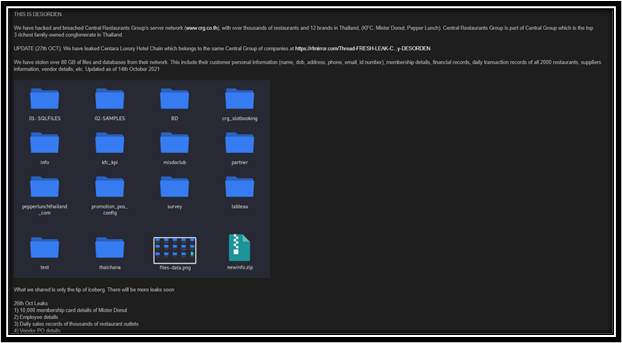
Central Hotel Group of Thailand confirmed through their website that they had been breached and were first aware of it on 14th October 2021.
400 GB of data was stolen and offered for sale on the Dark Web. This included all financial data, corporate data, employee data and more. There were a total of 5 production servers that had been wiped from the network by the APT group.
This attack appears to be part of a larger attack on Central Group companies, which includes Central Retail Corporation (which is listed on the Stock Exchange of Thailand) and Central Restaurants Group.
Current Exploit Strategy
The DESORDEN group which stands for chaos & disorder in spanish, was previously known as “chaoscc”. This notorious apt group uses trojan type malware as part of their tool set to breach an organization. The DESORDEN group mainly targets supply chain networks and public services. They are well known and responsible for several attacks in 2021.
The Desorden Group is capable of attacking and compromising supply chains by creating high levels of disorder & chaos that affect many parties apart from the victim itself. If the victim fails to comply with their demands, the data will be offered for sale on black market in a few days.
An investigation by Centara Hotels & Resort has confirmed that the threat actor has indeed compromised the system and accessed customer data. The data is described as photos of customer identification documents, name, booking information, phone number, email address, home address, and login ID’s. It is possible that the threat actor has also obtained customers passport information as these are frequently requested by hotels.
The Desorden Group stole more than 400 GB of data over the course of 10 days which includes information on patrons who stayed at 70 luxury hotels owned by the Thai conglomerate between 2003 and 2021. This also includes data from customers who booked in advance until December 2021.
Past Victims of the DESORDEN Group
- Taiwanese computer giant Acer has confirmed that its offices in India were breached by Desorden threat group affiliates, who stole 60GB of data.
- Lion City Employment Agency hacked by Desorden and about 40,000 personal data leaked.
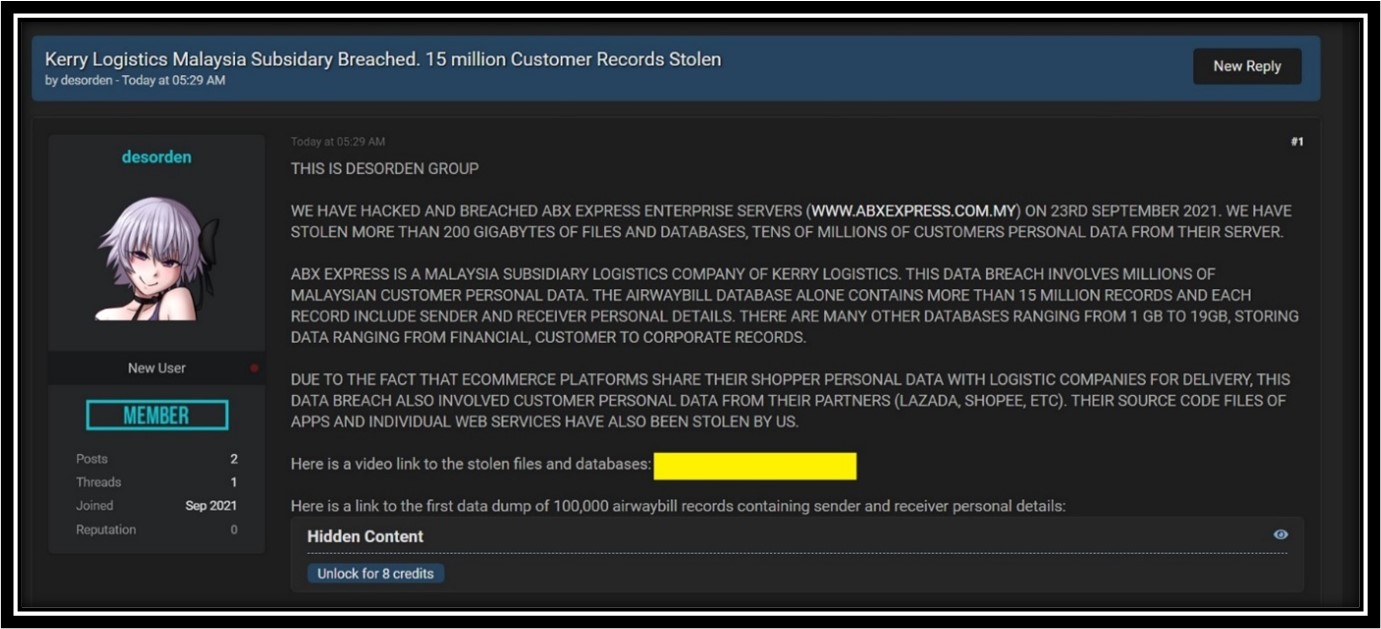
- ABX Express Enterprise has confirmed that 200 GB of files and data has been breached by Desorden.
- Sextortion Scheme Deployed by ChaosCC Hacker Group Demands US$700 in Bitcoin
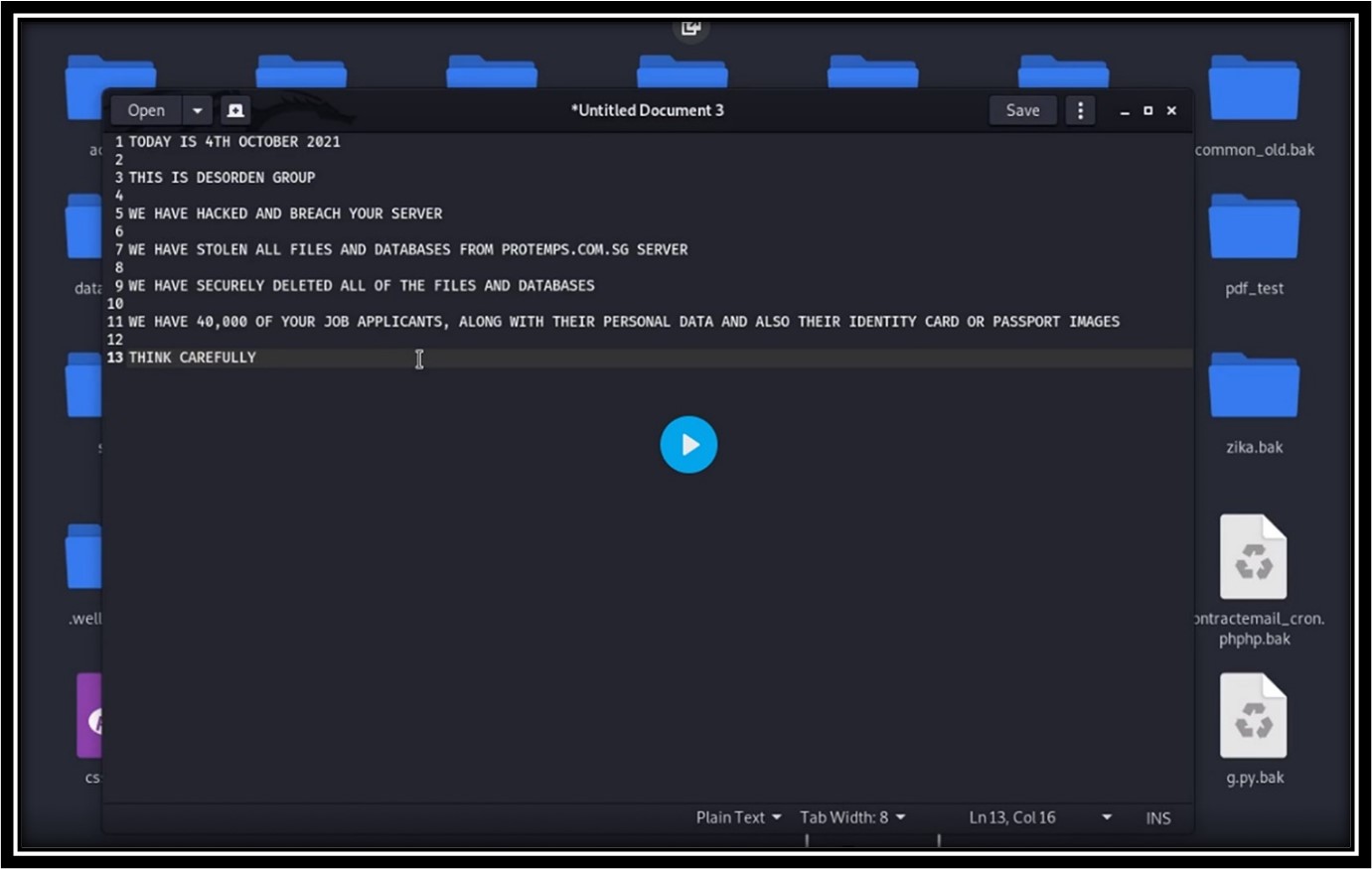
Ransom Notes from DESORDEN Group

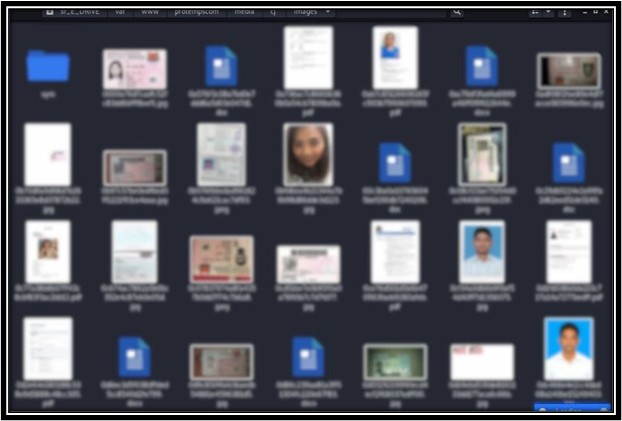

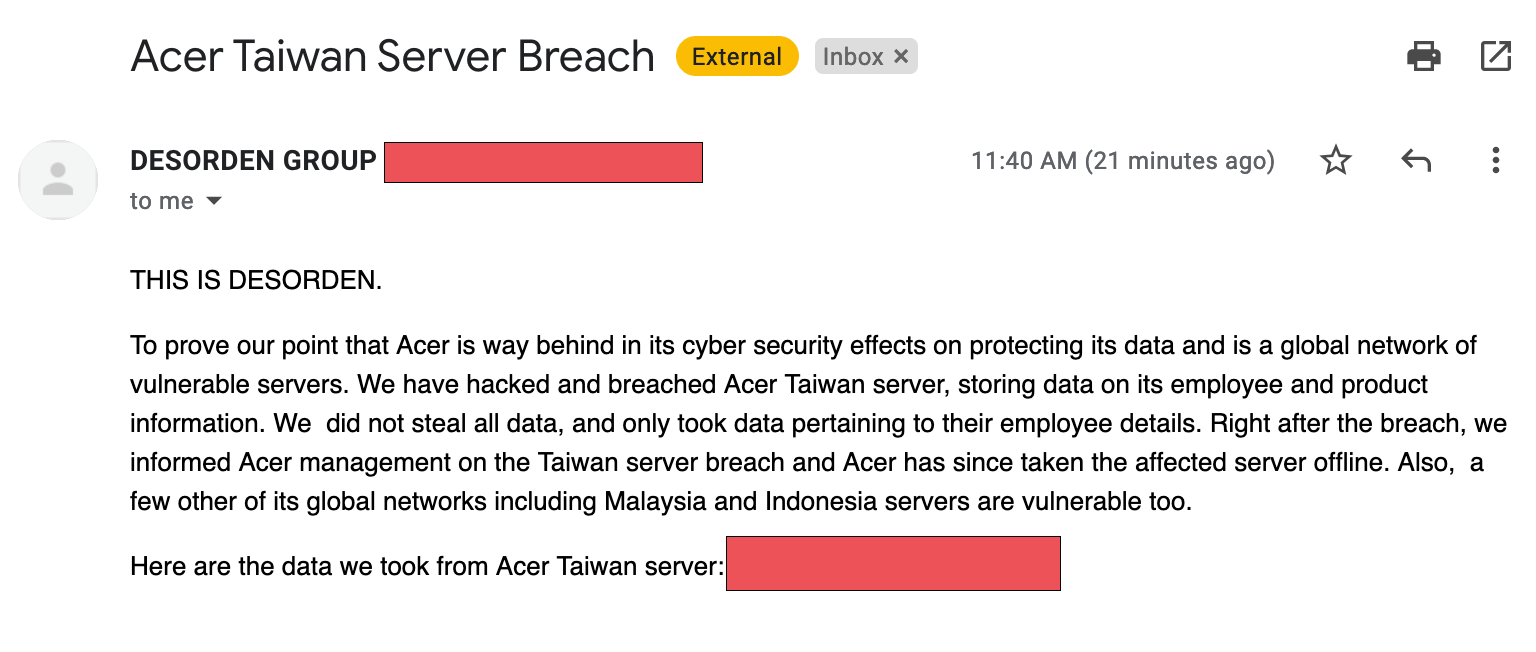

Impact of the Major Supply Chain Cyberattacks
Cyberattacks and security breaches are on the rise and the supply chain is at the forefront of these attacks. Threat actors are increasingly taking advantage of poor security practices found in organizations as a path to gain access to compromise the network. Here are the Top 5 major risks and impact on the digital supply chain.
1. The Human element
Whether it’s intentional or unintentional, people who do not follow procedures or don’t perform checks and balances can pose a significant risk to their own organization as well as the entire supply chain. Social Engineering attacks exploit psychological weakness like trust, anxiety and curiosity. Threat actors can socially engineer their way into obtaining access to email systems, gain an understanding of the policies and procedures, pretend to be a supply chain vendor and deceive businesses into wiring them large sums of money.
2. Critical Data
Supply chain attacks have been known to steal sensitive data from partners of business and governments. As illustrated by recent attacks on COVID-19 vaccine supply chains to steal vaccine information, nationwide attackers and organized cybercrime syndicates seek to exploit trade secrets and intellectual property.
3. Third-party and weak links
Manufacturing facilities use third-party providers to manufacture some of their products and digital businesses have adopted the use of third-party tools to build their products and services. Payments, analytics platforms, chatbots and advertising or social media integrations have introduced new risks to the business and make it challenging to protect critical data and ensure data privacy. Most websites have unsupervised third-party JavaScript integrations and lack adequate cybersecurity controls against Magecart, FormJacking, cross-site scripting and credit card skimming attacks. This is in an environment where the Covid-19 pandemic has forced global suppliers to adopt remote working and cloud computing for business continuity, collaterally introducing new security risks.
4. Lack of vendor risk management
The lack of a detailed understanding of the risks that vendors and third parties introduce to their environment make businesses prone to possible cyber attacks. Businesses must adopt a strict vendor oversight and monitoring process to run their operations with confidence in their ability to thwart a cyber-attack. Vendors should be ranked based on risk attributes which include reputation, financial, operational, regulatory, privacy and legal metrics. Their risk profile must be regularly assessed for changes. As risk evolves, the processes should also evolve in tandem.
5. Absence of Monitoring tools
It is essential to adopt real-time monitoring tools in order for an organization to run operations smoothly. Monitoring is crucial because it tracks historical events and incidents to facilitate planning for better mitigation and remediation. In order to do this, an organization needs to adopt a risk and compliance frameworks known as GRC (Governance, Risk and Compliance) platforms. The absence of a GRC platform can derail an organization’s security program. Businesses need to ensure that employees understand the sensitivity of data and follow security best-practices to adhere to and stay within guidelines. This also facilitates compliance with regulations. Businesses also need to have an incident response plan and ensure all the key stakeholders are involved.
Remediation and Mitigation Plan to Take During an Attack
1. Collect information from all the stakeholders.
Asset information details are important in that it facilitates review of how many endpoints are affected. This includes information such as servers, endpoints and user accounts which have been compromised in an organization.
Businesses are advised to remove the affected devices or servers from the network by way of network or firewall rules.
2. Limit the number of suppliers you use
It is a lot easier to manage access control for a few external parties rather than many.
3. Secure the backup storage
Store the server backup on a separate network until the incident response initiates the recovery process. Allow the security team to perform 1st level investigations on the effected endpoints to identify the root cause.
4. “Do Not Pay” Ransom
Business stakeholders are advised not to pay the ransom amount that may be requested by the threat actors. There is no guarantee you will retrieve the data in question and there are possible scenarios where the threat actors could still be lurking in your environment.
5. Bringing in an Incident Response Team
Provide access to the IR Team to perform an assessment on the affected environment as well as the operational environment so they can track down the lateral movement of the attack and gather information such as files that have been used for the attack. The team should be able to restore the environment subject to the severity of the attack.
6. Share information on how to improve
Let your suppliers know what you and others in your industry are doing to improve your data security so that they can adopt similar measures.
Prevention Plan from Cyberattacks
1. Security patching.
Ensure all the endpoints and devices connected to environment are patched regularly. This is a “best-practice” through which you can close the gateways used by threat actors in most recent exploits.
2. Fully understand the threat to the supply chain business.
This practice allows the team to completely review, learn, and keep track of all supply chain breaches, data leaks, and malware attacks that affect the company.
3. Assess your cybersecurity measures.
Cybersecurity applies a risk-based strategy to prevent and adjust to invasions of the system. The team needs to know what measures are already in place and which are missing. This Framework includes hardware used to prevent or mitigate an incursion, software used on network computers, and much more. This approach should also include knowledge of the company’s cybersecurity plans.
4. Improve current measures.
Once you have the full picture of current security measures, it’s time to improve tools and processes. This may include purchasing a more advanced security appliance. The strategy team may need to install or update software on all computers or push AI to a centralized location to learn how data moves within the enterprise system.
5. Treat cybersecurity as an ongoing process.
Once the security measures have been increased, you will need to document, review, and sift through feedback. This will provide you with a knowledge base that will enable you to share current vulnerabilities and mitigation plans for cyber-situations. The process to maximize cybersecurity is always evolving. Once an attack is over, a new development may require upgrades to prevent future infiltrations.
Cybots Solutions
Cybots offers a complete suite of security services for your Cyber Security needs. This includes the key elements of Compromise Assessment (CA), Incident Response and Fast Forensic Services (IR & FFS), Threat Intelligence and Advanced Managed Detection and Responses (AMDR).
- Detailed and Accurate Reports.
- Site-wide Analysis
- Guided walk-through of all reports.
Incident Response and Fast Forensic Services (IR & FFS)
- Guided walk-through of Reports within 1 day of scanner runs
- Assurance of Data Privacy and Zero Data Leakage during the process
- Self-updating Global Threat Intel Platform
- References Global Library of breaches and methods
- Complete information security dictionary to support 14 categories of threat indicators
- References over 20 threat intelligence sources
Advanced Managed Detection and Response (AMDR)
- Scheduled Automated Reports
- Auto-Triaged Alerts
- Automated Investigations
- Actionable Reports and Storyline (Lateral Movement)
Our solutions are able to detect and mitigate a Cyber Attack at an early stage. We provide insight reports that increase situational awareness and understanding. We also offer bespoke customer cybersecurity services on request.
References
- Notice of Data Security Incident (source : Centara Hotel Resorts press release)
- Cybertotal Threat Intelligence