In a year of threat landscape defining vulnerabilities (ProxyLogon, Log4j) and supply chain attacks with never before seen blast radiuses (SolarWinds, Kaseya), one threat has been consistently booming in the most recent years, dominating much of the cybersecurity dialog in both 2020 and 2021 — ransomware.
While not new to the cyber threat landscape, ransomware’s impact on businesses has grown some considerably vicious teeth in recent years, with reported cases of targeted companies now paying ransoms in the millions.
According to FinCEN (the U.S. Treasury’s Financial Crimes Enforcement Network), there was 590M USD in ransomware-related activity in the first six months of 2021 alone.
Although the decade-long growth of cryptocurrency has undoubtedly fueled the frequency of ransomware attacks, recent trends such as double extortion, the rise of the ransomware-as-a-service (RaaS) business model, and successful “big game” ransomware attacks have all helped to drive ransomware to the forefront of the cyber threat landscape, the daily online infosec discussion, and international news organizations.
When not discussing the latest ransomware incident response reports or how many millions in ransom the latest ransomware victim paid, one question repeatedly pops up in discussions:
How do you combat this digital pandemic of ransomware attacks?
The rocky road to constructing an effective novel response against ransomware begins with understanding the recent trends of the underground ransomware ecosystem, common targets of ransomware, typical ransomware behavior, common ransomware encryption schemes, decryptor construction and application, and integration with defender protocols and tools.
In this upcoming series of articles, we will discuss each of these factors one by one.
Recent Trends of the Ransomware Ecosystem
The romantic days of the lone hooded hacker frantically typing away in a dark basement full of servers and wires have long since passed. The cybercrime underground is a diverse ecosystem with specialists in every possible field. Ransomware today operates similarly to any professional SaaS business. And business has been booming.
Although the wider accepted use of cryptocurrency has undoubtedly fueled the frequency of ransomware attacks more than any other factor, other trends have emerged in recent years as attackers undoubtedly discovered these techniques yielded higher profit margins.
Double Extortion
After WannaCry and NotPetya (2017), enterprises put more effort into improving data backup and restoration processes; therefore, if any data were to be encrypted, the enterprise could easily get back to business without the need to pay the ransom. However, Maze (2019) and Sodinokibi (2020) encrypted and exfiltrated sensitive data, so if the targeted enterprise did not pay the ransom, the exfiltrated data would be leaked or sold online. Other ransomware gangs quickly followed suit. Double extortion not only increases the attacker’s potential revenue but also applies added pressure on the victim to pay the ransom faster.
Supply Chain Attacks
While not new to the threat landscape, the modern supply chain attack has not only a far greater blast radius but also a far more severe impact than supply chain attacks a decade ago. Solar Winds, Microsoft Exchange Server, and Kaseya are all prime examples of how one attack on a supplier can directly affect thousands of their customers’ environments.
“Yes, this [targeting organizations that have cyber insurance] is one of the tastiest morsels. Especially to hack the insurers first — to get their customer base and work in a targeted way from there. And after you go through the list, then hit the insurer themselves.”
“Unknown”, REvil Representative
Cybercriminal Ecosystem Specialization
One ransomware attack is seldom the work of solely one group, nor does the appearance of one kind of ransomware or tool immediately attribute the attack to said ransomware gang. One ransomware attack could be jointly operated by a number of stand-alone groups or affiliates, with each receiving a percentage of the ransom paid.
Each affiliate could be responsible for one aspect of the attack, such as initial access, ransom negotiations, money collection, money laundering, or target reconnaissance. Cybercriminals no longer need to be solely responsible for the entire attack, but can now outsource each phase of the cyber kill chain to an affiliate for a cut of the profits. Even banking Trojans such as Emotet and Trickbot have been leveraged to deploy ransomware.
Naturally, all these factors complicate the attribution process for investigators.
Ransomware as a Service (RaaS)
Make no mistake. RaaS is a growth industry, with some analysts estimating total ransomware revenue in 2020 exceeding 20 billion. While some RaaS groups simply sell their ransomware on the dark web, others more closely follow the SaaS service model, selling their ransomware to their affiliates for a cut of the profits.
Cybercriminal groups without enough time or resources to develop their own ransomware variants can be operational quickly, gaining access not only to the ransomware itself but also an entire platform covering multiple aspects of a ransomware attack, including negotiation, collection, and/or laundering of ransoms.
Our next stop on the road to ransomware resilience leads us to recent trends in victim selection. Who are ransomware gangs targeting? Who is most at risk? Unfortunately, we didn’t have to travel too far.
Ransomware in Taiwan & Japan
Due to its rather distinctive geopolitical situation, Taiwan frequently encounters the most sophisticated, persistent, and aggressive threats before the rest of the world.
One case in point was when APT (Advanced Persistent Threat) Chimera invested in a year-long attack campaign targeting Taiwan’s semiconductor ecosystem, and then appeared in the EU the following year using the same tools and techniques.
These advanced threats — often state-sponsored, state-ignored, or criminal syndicate actors — typically focus their efforts on Taiwan to test their newest, most subtle, and most malicious techniques.
In the last few years, ransomware attacks have increased in frequency and severity; in one instance, ransomware was even used as a diversionary smokescreen technique to mask the attackers’ true goals in an attack on Taiwan’s critical infrastructure.
Below is a partial list of the more severe and most recent ransomware attacks with targets located in either Taiwan or Japan.
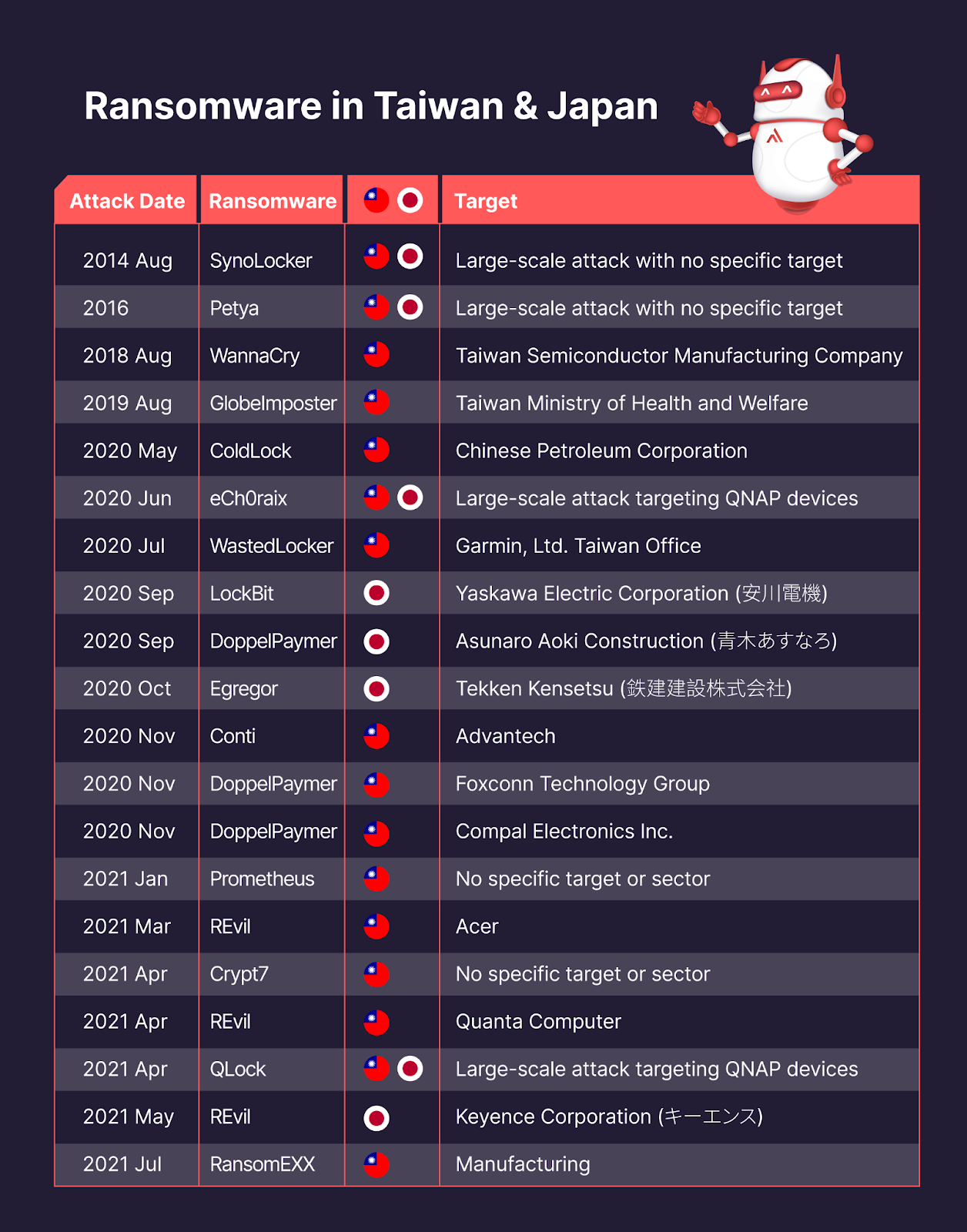
Fig. 1 — Notable Ransomware Attacks with Targets in Taiwan and Japan
Within this short time frame, we already see two main styles of ransomware emerge — traditional and big game.
For decades, ransomware wasn’t that profitable. Traditional ransomware typically focused on large-scale worldwide attacks with no specific targets. Ransoms would be in the hundreds of dollars and, for the briefest of times, could even be paid in prepaid charge/debit/gift cards.
However, the last few years have seen ransomware shift towards big game hunting where one singular victim is targeted — typically an enterprise with over a billion in annual revenue. Ransomware gangs have traded in catching multiple small fish for catching one big fish, and big fish pay millions in ransom.
In both Taiwan and Japan, organizations in high-tech and manufacturing have both seen a significant spike in risk these past few years. Ransomware gangs have not only targeted both these industries but have done so in rapid succession.
“It’s definitely changed. The crisis [the pandemic] is palpable; they [victims] are not able to pay the same amounts as before. Except for manufacturers of pharmaceutical products. I think it is worth paying more attention to them.”
“Unknown”, REvil Ransomeware Representative
In Japan, in the span of 2 months, at least 3 major enterprises in high-tech or manufacturing (Yaskawa Electric Corporation, Asunaro Aoki Construction, and Tekken Kenetsu) were targeted and attacked by 3 different ransomware gangs in 2020.
In Taiwan, in a span of 6 months (November 2020 to April 2021), at least 8 enterprises in high-tech or manufacturing were targeted and attacked by 6 different ransomware gangs.
Manufacturers are often targeted due to their high-profile customers. Targeting the manufacturer provides ransomware gangs the opportunity to extort money from both the manufacturer and their high-profile customers.
Compal is the second-largest original design manufacturer (ODM) for laptops in the world and provides laptops for several high-profile customers, including Apple, Lenovo, Dell, Toshiba, HP, Fujitsu, and Acer. In November 2020, Compal was hit with a 17M USD ransom demand from DoppelPaymer — the same ransomware gang that had also hit electrons giant, Foxconn, with a 34M USD ransom that same month.
It should come as no surprise that Acer, one of Compal’s customers, was hit with a 50M ransom by REvil only 4 months after the Compal attack. Then, only one month later, REvil attacked the largest ODM of laptops — Quanta.
Quanta supplies numerous high-profile customers such as Apple, Alienware, Cisco, Microsoft, Dell, and Hewlett-Packard.
In April 2021, REvil attempted to extort Quanta for 50M USD in return for stolen Apple product blueprints. When Quanta refused, REvil immediately began talks with Apple over the exfiltrated data. When REvil approached Apple, REvil leaked a handful of schematics of unreleased MackBook components onto the dark web. Since the initial leaking of the stolen documents, no additional images have been leaked online.
However, the trends of ransomware go beyond their targets’ industries. Our next stop on the road to ransomware resilience goes deep into the ransomware itself as we will explore typical ransomware trigger behavior and common ransomware encryption schemes.
If you’re interested in learning about compromise assessments to ensure the health and security of your network, contact us.