Taking The Significant Alerting Lead in MITRE ATT&CK® Evaluations’ Latest Round
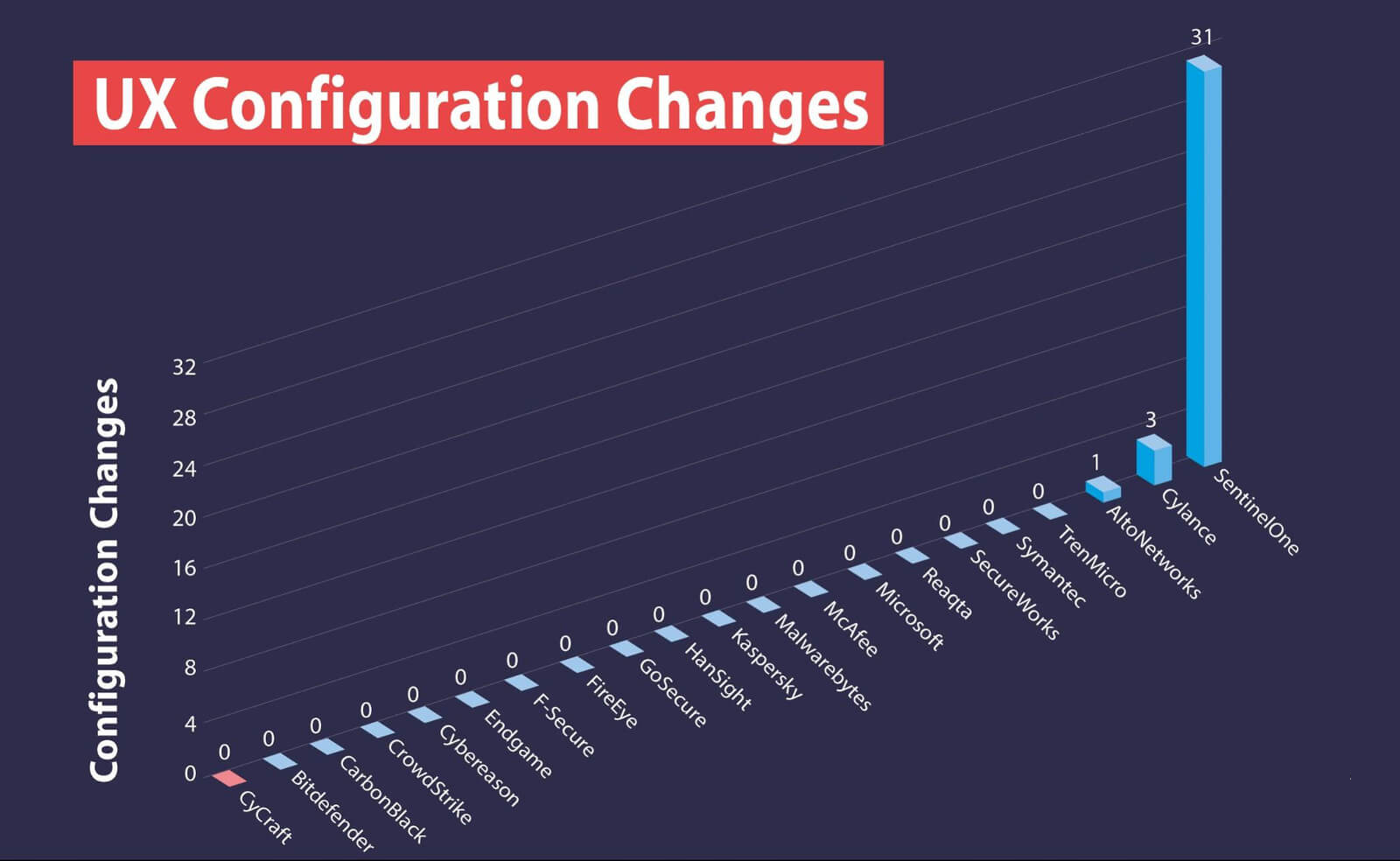
With zero configuration changes, our AMDR rose far above the competition to deliver the most alerts of any vendor.
A leader in artificial intelligent automated SOC operations and endpoint security, announces our results from round two of the MITRE ATT&CK® Evaluations. We received the most alert detections out of the 21 participants validating our world-leading thoroughness, accuracy, and results-oriented focus.
Number One in Alerting
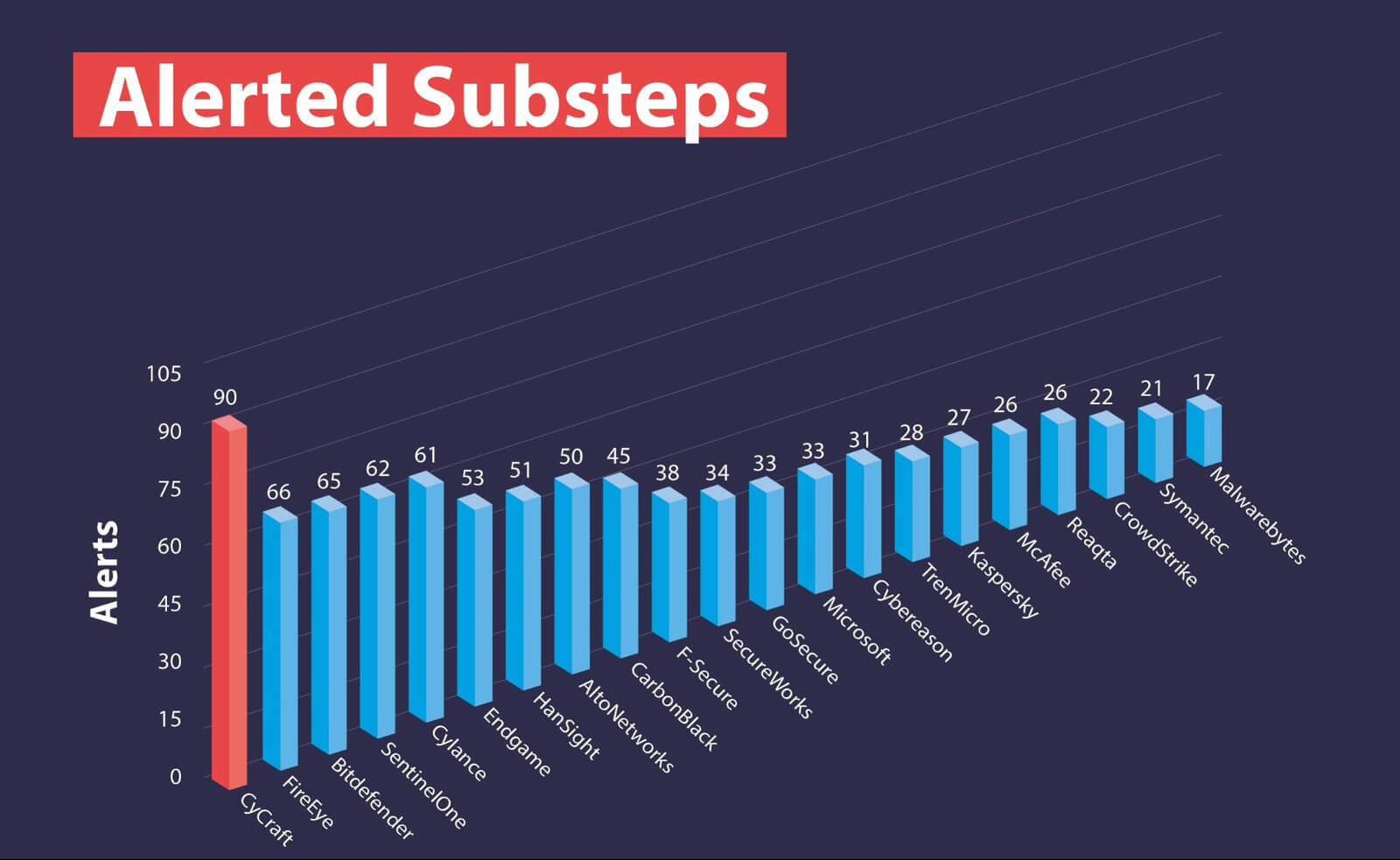
In achieving its goals to be fast, accurate, simple, and thorough, our AI generated the most accurate and thorough alerting among the evaluation participants. With alerts on 90 substeps in the evaluation, including General, Tactic, and Technique detections as per MITRE distinction, we provided the most complete alerting against the Advanced Persistent Threat 29 challenge. Alerts show that rather than just passively detecting adversary behavior, a vendor is capable of prioritizing that behavior and communicating it to the SOC operations team so they are able to act on it.
Zero Configuration Changes
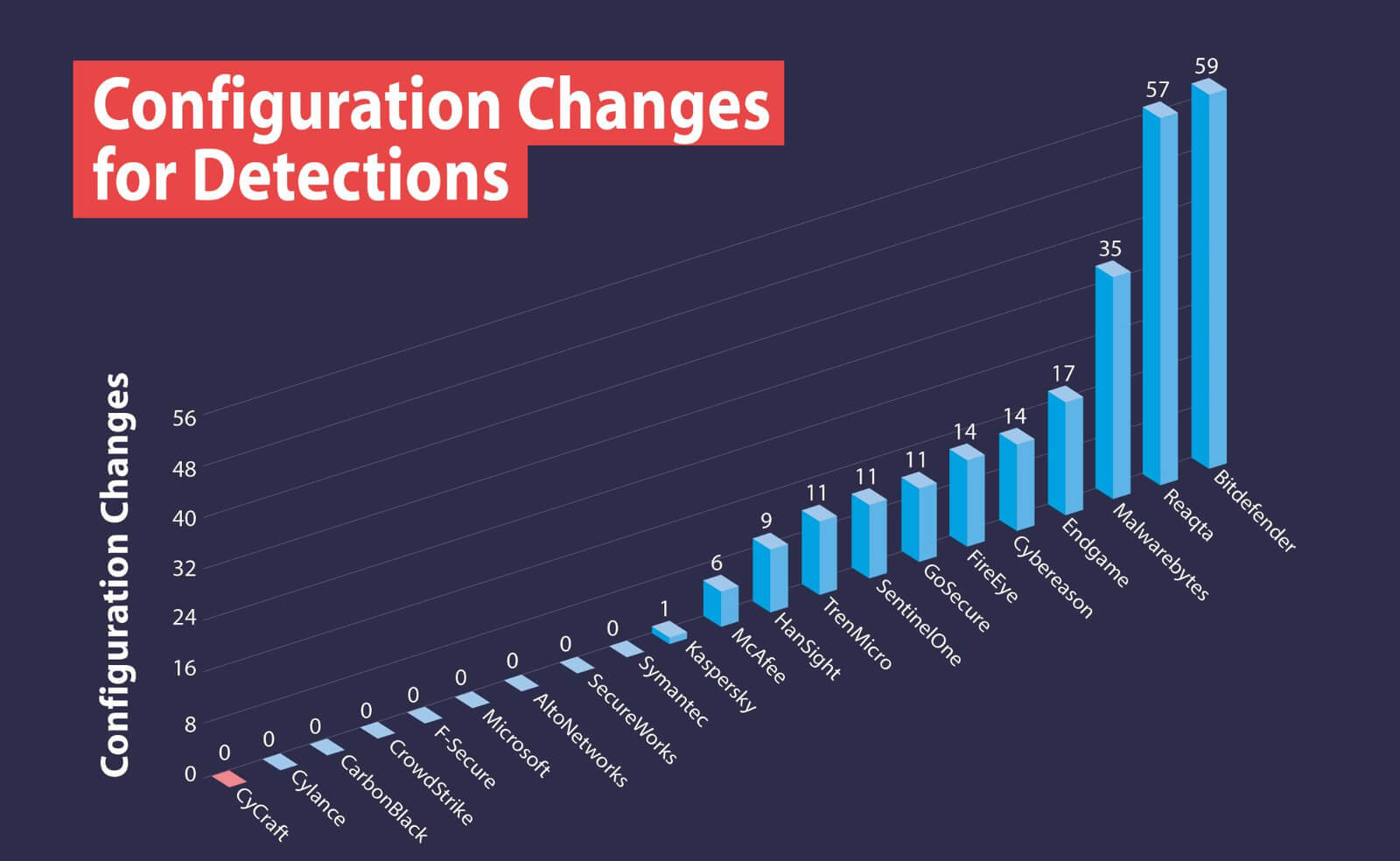

User- and results-focused, we generate all of the alerting with zero configuration changes.

A New Perspective on Telemetry
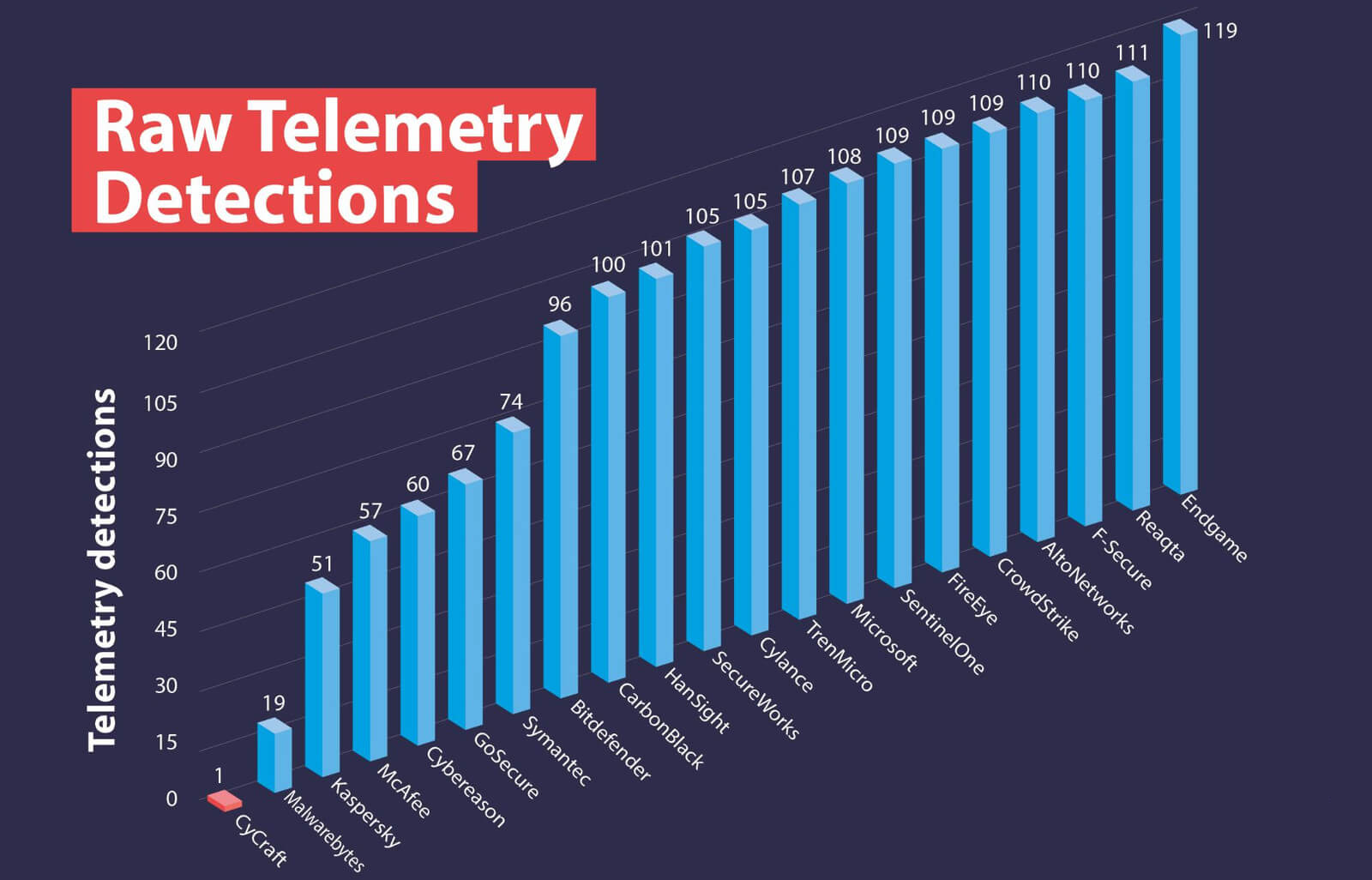

MITRE ATT&CK & APT29
“We view the evaluations as a collaborative process to help the participating vendors improve their products, which ultimately makes cyberspace safer for everyone,” said Frank Duff, ATT&CK Evaluations lead. “Taken as a whole, the results indicate that the participating vendors are beginning to understand how to detect the advanced techniques used by groups like APT29, and develop products that provide actionable data in response for their users.”
Since the ATT&CK APT29 Evaluation of 2019, we further automated and sped up its alerting with a new version of its MDR AI engine and released its enterprise prevention and protection platform with NGAV for real-time blocking of suspicious and known threats. We will be participating in the next round of evaluations against emulations of financial institution-targeting adversaries Carbanak and FIN7.
“We see the ATT&CK Evaluations as a great playing field leveler. Finally, there is a place for vendors to go head-to-head in a transparent way that is meaningful to buyers, and the rest of the industry—a veritable blue-team cyber colosseum for leading products around the world to benchmark their true capabilities. End users are often overwhelmed with marketing buzzwords and frustrated in the dearth of concrete info when comparing products to avoid redundant, weak, or non-existent capabilities. With the MITRE evaluation and accompanying matrices, end users, vendors, buyers, and the industry at large now have a lexicon and a map to best spot, detect, respond to every move, and communicate effectively when facing sophisticated attacks,”
About ATT&CK
ATT&CK® was created by MITRE’s internal research program from its own data and operations. ATT&CK is entirely based on published, open-source threat information. Increasingly, ATT&CK is driven by contributions from external sources. Cybersecurity vendors may apply to participate in the next round of the ATT&CK Evaluations, which will feature the Carbanak and FIN7 threat groups as the emulated adversaries.