Lockbit2.0, beyond privacy and security
This document describes the recent Cyber Attacks on Accenture that reportedly affected over 2,500 computers and leaked client information. LockBit threat actors posted the names of companies and their logos on their dark web site. They threatened to publish the data stolen during the Accenture ransomware attack. The threat actor suppressed Accenture’s current security practices and described them as “beyond privacy and security”.
Current Exploit Strategy
Researchers claimed that the ransomware operators have stolen a database containing over 6TB of data and are demanding $50 million in ransom from Accenture. There is some speculation that an insider had helped the gang gain access to the network at the consulting firm.
The data was displayed on a leak site with countdown after disclosure of the attack. The threat actor group threatened to publish files purportedly stolen from the company. Once the countdown had expired, the ransomware gang published a small set of stolen data composed of 2,384 items. The leaked files included confidential PDF documents which were stolen from the company.
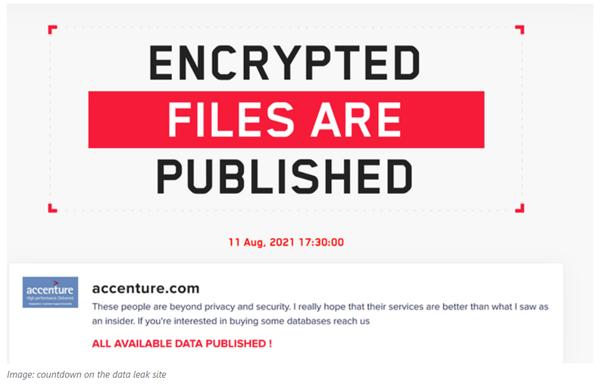
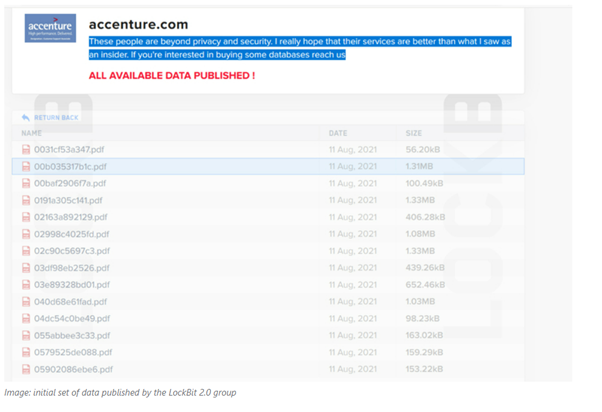

The ransomware operators removed the above files and extended the countdown to August 18, 2021.
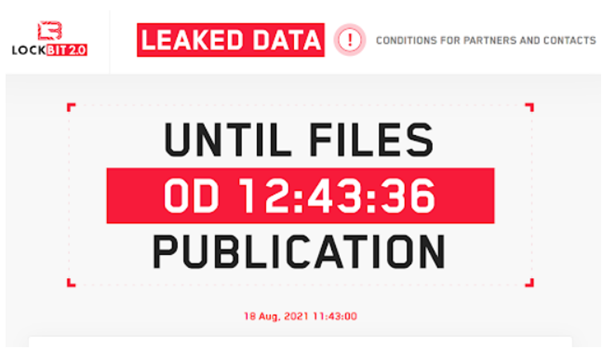

The extension of deadline for publishing the stolen data could suggest two scenarios:
• The ransomware operators have started a negotiation with Accenture to avoid the stolen data being published.
• Ransomware operators did not steal sensitive data from Accenture during the attack and are using the story to increase their visibility in the threat landscape.
Mitigation Plan by Accenture
Once Accenture detected this abnormal activity in their environment, the company informed that they had isolated the infected servers and endpoints from their network and restored impacted systems from their backups. According to Accenture, they identified and reviewed their security controls & protocols. Based on the investigation, Accenture’s security team identified irregular activity in environment and immediately contained the matter and isolated the affected servers.
LockBit2.0
The LockBit ransomware-as-a-service (RaaS) gang has ramped up its targeted attacks. Their most targeted countries are Chile, Italy, Taiwan and the U.K., using the 2.0 version of their malware.
The new version of LockBit added new attack methods and features by itself. This version automates encryption of devices across Windows domains by abusing Active Directory (AD) group policies. The group behind it claimed that LockBit 2.0 is one of the fastest ransomware variants in the market today. Cybots’ analysis of this malware indicates it is capable of using a multithreaded approach to encryption which allows it to partially encrypt the files. Only 4KB of data are encrypted per file.
LockBit ransomware is considered by many authorities to be part of the “LockerGoga & MegaCortex” malware family. This implies that it shares behavior with these established forms of targeted ransomware:
• Self-spreading within an organization rather than requiring manual direction.
• Targeted rather than spread in a scattershot fashion like spam malware.
• Using similar tools to spread, like Windows PowerShell and Server Message Block (SMB)
Stages of LockBit Attacks
We classify LockBit into three stages:
• Stage 1: Exploit
• Stage 2: Infiltrate
• Stage 3: Deploy
Stage 1: Exploit weakness in a network. An organization may be exploited by social engineering tactics like phishing.
Stage 2: Infiltrate deeper to complete attack setup if needed. The goal of infiltration is to make unassisted recovery impossible, or slow enough that succumbing to the attacker’s ransom is the only practical solution.
Stage 3: Deploy the encryption payload. Once the network has been prepared for LockBit to be fully mobilized, the ransomware will begin its propagation across any machine it can touch.
Types of LockBit Threats (IOC)
The LockBit threat is a variant of concern for ongoing ransomware attacks. We cannot rule out the possibility that it can take hold across many industries and organizations. This is compounded by the recent increase in remote working. Identifying LockBit’s variants can help with pinpointing the scenarios.
Variant 1 – .abcd extension | Ransom note with demands and instructions for alleged restorations in the “Restore-My-Files.txt” file |
Variant 2 – .LockBit extension | Victims will find that other traits of this version appear mostly identical despite some backend revisions. |
Variant 3 – .LockBit version 2 | Sends victims to an alternate website via traditional internet access instead of the Tor Browser |
Indication of Compromise (IoC)
Payload Delivery Malicious Hash value
• A5434B72FA80D4ED2BEF826A36542DBC
• D4E3C16A2FFBFC3ED46ADEEA2F13D21EDC332B85
• E32DC551A721B43DA44A068F38928D3E363435CE0E4D2E0479C0DFDB27563C82
• 0859A78BB06A77E7C6758276EAFBEFD9
• 0D3058695E559B95910911C4B391D482
• 123511227718F17B3DEC5431D5AE87F3
• 13BAA52D7961DB198134763370AA61E7
• 1CD2D73098671253243A8457355B8820
• 1F4F6ABFCED4C347BA951A04C8D86982
• 1FBEF2A9007EB0E32FB586E0FCA3F0E7
Domain
lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd.onion | bigblog.at |
lockbitsap2oaqhcun3syvbqt6n5nzt7fqosc6jdlmsfleu3ka4k2did.onion | decoding.at |
lockbitsup4yezcd5enk5unncx3zcy7kw6wllyqmiyhvanjj352jayid.onion |
|
Remediation and Mitigation Plan
• Conduct an audit and inventory of the asset list.
• Patch and update the endpoints.
• Configure, monitor and manage hardware and software configurations.
• Protect and recover by enforcing data protection, backup, and recovery measures.
• Secure and defend by performing sandbox analysis to examine and block malicious email.
• Perform security skills assessment and training for all personnel regularly. Conduct red-team exercises and penetrations tests.
• Ensure the endpoints are patched with these vulnerabilities (CVE-2018-13379)