What is Managed Detection and Response?
The Benefits, How it’s Different, How to Choose a Vendor, and More
Managed detection and response (MDR) is a service that fulfills the needs of organizations that lack the time and resources to be fully capable of identifying risks and detecting, verifying, and responding to threats and/or security incidents.
According to Gartner, a global research and advisory firm, managed detection and response (MDR) vendors provide the following services:
- 24/7 threat monitoring
- Advanced analytics
- Threat intelligence
- Human expertise in incident investigation and response
- Detection and lightweight response services to customers leveraging a combination of technologies deployed at the host and network layers
MDR providers could also undertake incident validation, continuous monitoring of all IT assets, threat containment, remediation support, as well as other services; however, at its core, managed detection and response (MDR) services—sometimes referred to as threat monitoring, detection and response—provide customers with modern security operations center (SOC) capabilities to detect, investigate, verify, respond to, and analyze threats.
Wait.
Why did Gartner define “MDR provider” but not “MDR”?
Managed detection and response (MDR) is not a technology; it’s a service.
WHAT DO MANAGED DETECTION AND RESPONSE SERVICES PROVIDE?
Most organizations lack the time and resources to be fully capable of identifying risks and detecting, verifying, and responding to threats and/or security incidents. MDR services provide these organizations a turn-key solution to these problems.
For a time, the mean time to detect (MTTD) a threat was about 200 days—over half a year. However, modern MDR is now capable of detecting and dealing with threats as quickly as a few hours, if not faster.
This is one of many factors that has caused the managed detection and response (MDR) market to have grown significantly over the last few years, and it is projected to continue increasing.
In their 2020 Market Guide for Managed Detection and Response, Gartner predicted that by 2025, 50% of organizations would be using MDR services for threat monitoring, detection and response functions that offer threat containment capabilities.
Each managed detection and response (MDR) vendor offers their own unique set of tools and products to detect and respond to threats. In addition to providing MDR services, many vendors also provide other services, such as threat containment and remediation guidance.
However, before you go into the differences between each vendor, it’s best to understand the similarities between the offerings from managed detection and response vendors, as clever marketing could have you chasing after the same product again and again.
- Remotely delivered SOC capabilities. This should include access to technologies that focus more on high-fidelity threat detection, investigation, and response than compliance.
- Threat intelligence. This typically involves a compilation of open-source intelligence, intelligence from the dark web, and proprietary intelligence—be it internally sourced or subscription-based.
- Humans (Security Experts). Different degrees and methods of automation are implemented into each vendor’s solution; however, humans are still incorporated into the service and are needed to monitor and offer support 24/7. Vendors offer 24/7 support themselves, through a partner, or share the responsibilities with a partner. Either way, customers should expect to have some degree of direct communication with security experts instead of relying solely on portals or dashboards.
- Automated incident validation and response. As they are typically done with the same technology as MDR, most managed detection and response (MDR) service providers usually offer both remote compromise assessment (CA) and remote incident response (IR) services. You may only need a separate retainer for on-site incident response or compromise assessment.
Later in this article, we will discuss the differences between MDR vendors, how to evaluate MDR vendors, and how to determine which vendor is most suitable for your organization’s needs. First, we need to understand why MDR is important and what its benefits are.
WHAT ARE THE BENEFITS OF MANAGED DETECTION AND RESPONSE?
In 2016, there were 2 million unfilled cybersecurity positions, a number that is expected to rise to 3.5 million by the end of 2021.
Running an effective, fully in-house security operations center (SOC) is a highly complicated endeavor that requires a plethora of tools and roles to fully and confidently execute. SOCs, unfortunately, often prove to underperform and be too resource-intensive for all but the largest organizations.
Yet even for larger organizations and enterprises, running an effective SOC is still fraught with so many communication, visibility, role, resource, cross-departmental, and complexity concerns (in addition to other internal considerations) that many organizations turn to MDR as a single turn-key solution.
“The first time I took the CISO role was at Facebook. I got great support from the executive leadership, an almost unlimited budget, the ability to grow and hire great engineers, and buy technology. But the most surprising thing is that you realize you can’t buy your way to good security. You literally can’t write a blank check and have great security tomorrow. Security requires long-term investment. It requires you to run alongside the development teams and the business teams, understand them, and help them reduce their risks.”
Joe Sullivan, former CSO at Uber and Facebook, now at Cloudflare, a16z podcast, episode 548
MDR focuses on detection, not compliance and not org-wide security protocols.
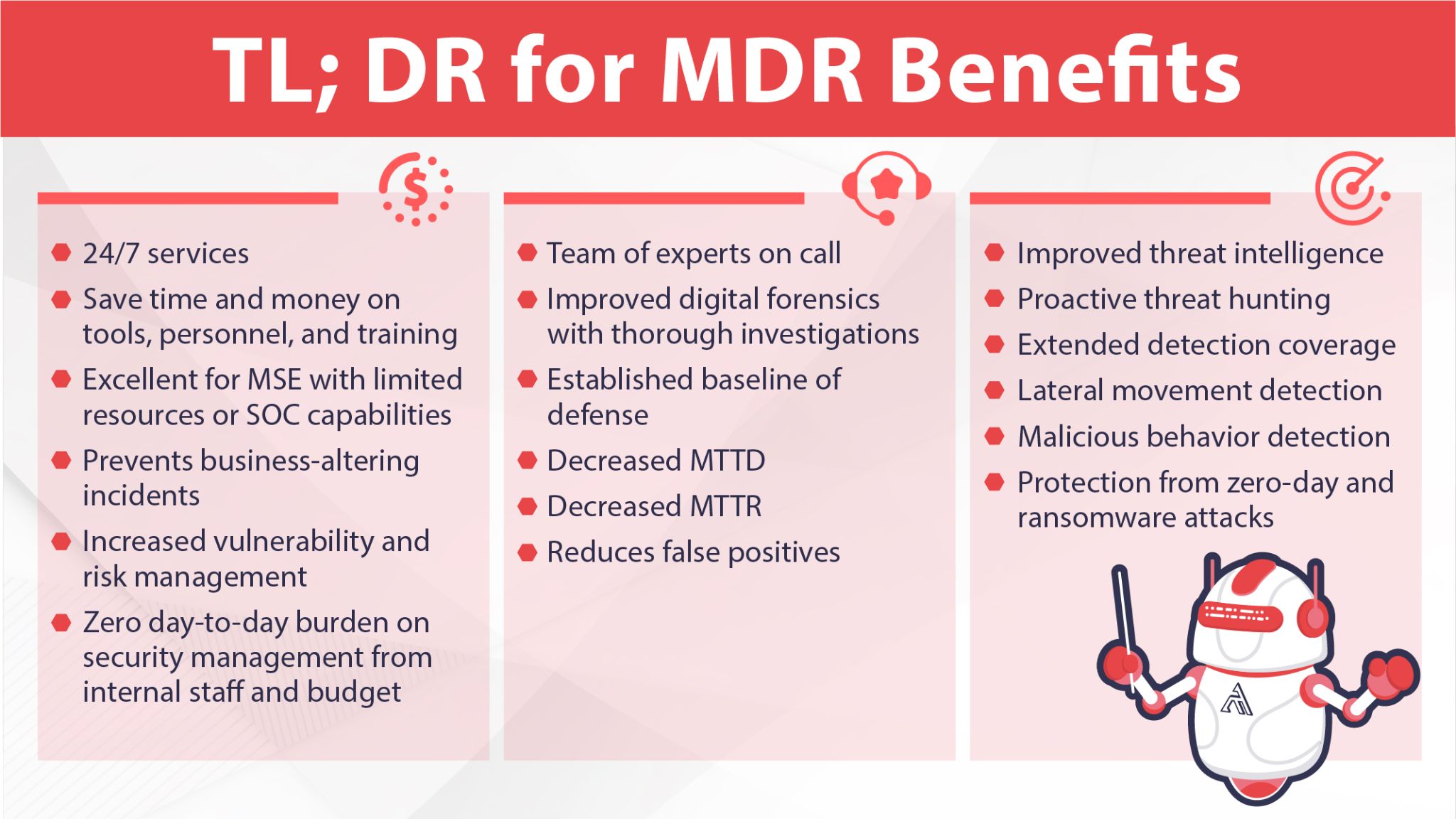
Much like other outsourced services, managed detection and response service providers offer you access to a team of experts for a discounted and affordable price. Additionally, MDR services typically include a multitude of monitoring, security, and perimeter detection tools—all attempting to detect intrusions as soon as they occur, preventing major damage to the rest of the network.
MDR addresses several key challenges for organizations, including the lack of qualified personnel, sophisticated targeted attacks, ransomware, complicated endpoint detection and response (EDR) tools.
Organizations in 2021 and beyond will face more and more pressure to increase cybersecurity resilience as more countries and insurance companies are taking stronger and stricter stances on ransomware attacks, such as French insurer AXA, who claimed they would no longer help companies pay for ransomware. On the other side of the globe, Ransomware Payments Bill 2021 would force Australian enterprises to disclose ransomware payments to the Australian Cyber Security Centre (ACSC).
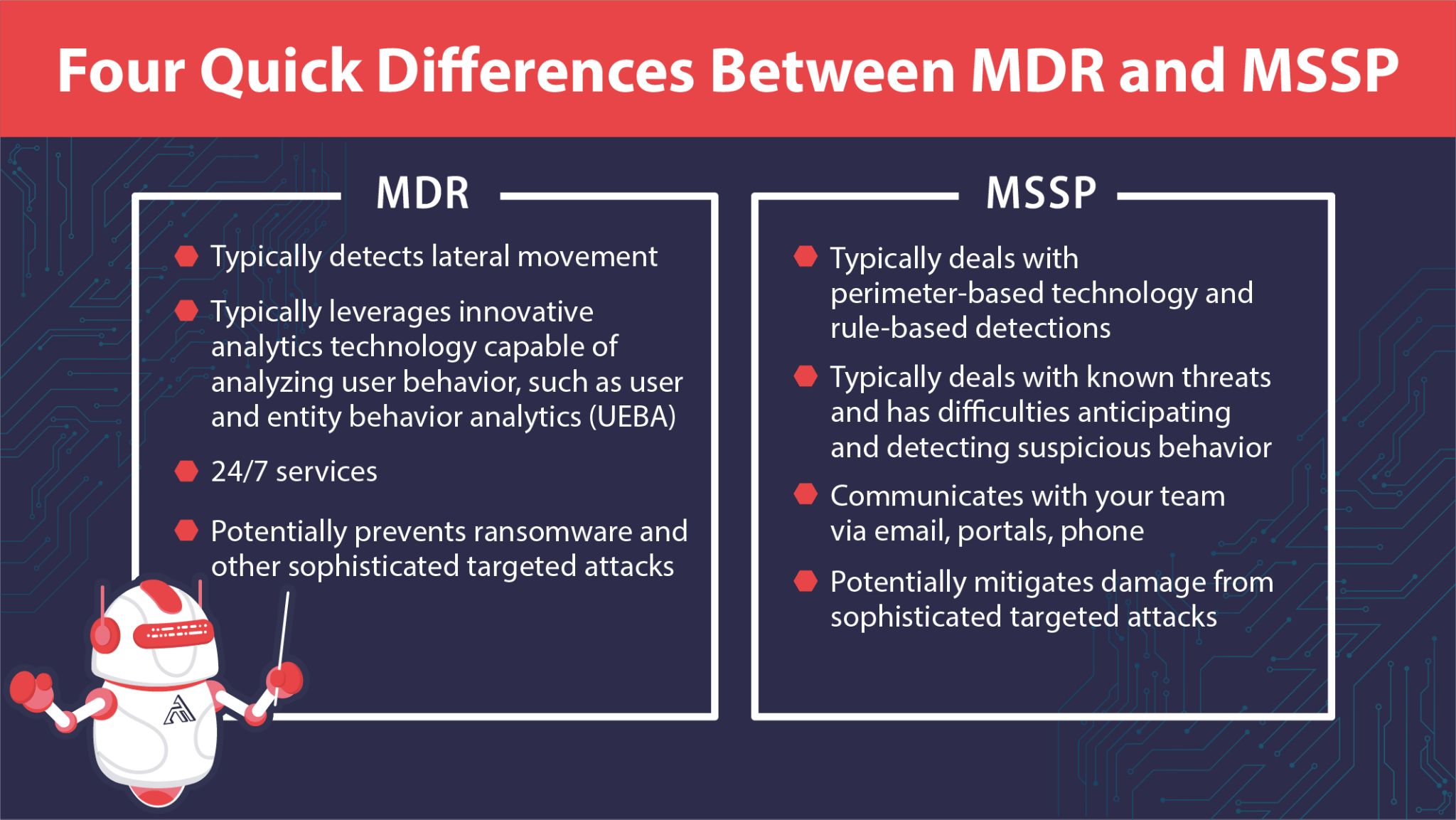
MDR providers help your organization avoid sophisticated targeted attacks from escalating into business-altering security incidents; traditional managed security service providers (MSSPs) might not be prepared for the degree of sophisticated attacks MDR providers have experienced in the wild. Here are four quick differences between MDR and MSSP.

Yet another benefit of MDR services is that providers often perform all the testing, threat hunting, sandboxing, and remediation for you. If an artifact or malware is detected in your system, you may only need a separate retainer, if not already included in your service, for eradication and remediation services.
There is an ocean of publicly available and/or subscription-based threat intelligence providers out there, not including all the threat intel from red and blue teams on social media. Even larger organizations have difficulty keeping their heads above water with list after list of indicators of compromise (IoC)s. Yet another benefit of MDR service providers is that they often include up-to-date threat intelligence and perform this updating for you.


WHAT SHOULD YOU KEEP IN MIND WHEN SELECTING A MANAGED DETECTION AND RESPONSE VENDOR?
You need to enhance your organization’s cybersecurity posture. You’ve researched the need for and benefits of managed detection and response (MDR). Now, you’re ready to begin evaluating different MDR vendors and their offerings. Here are six things to keep in mind while going through all the marketing material and buzzwords.
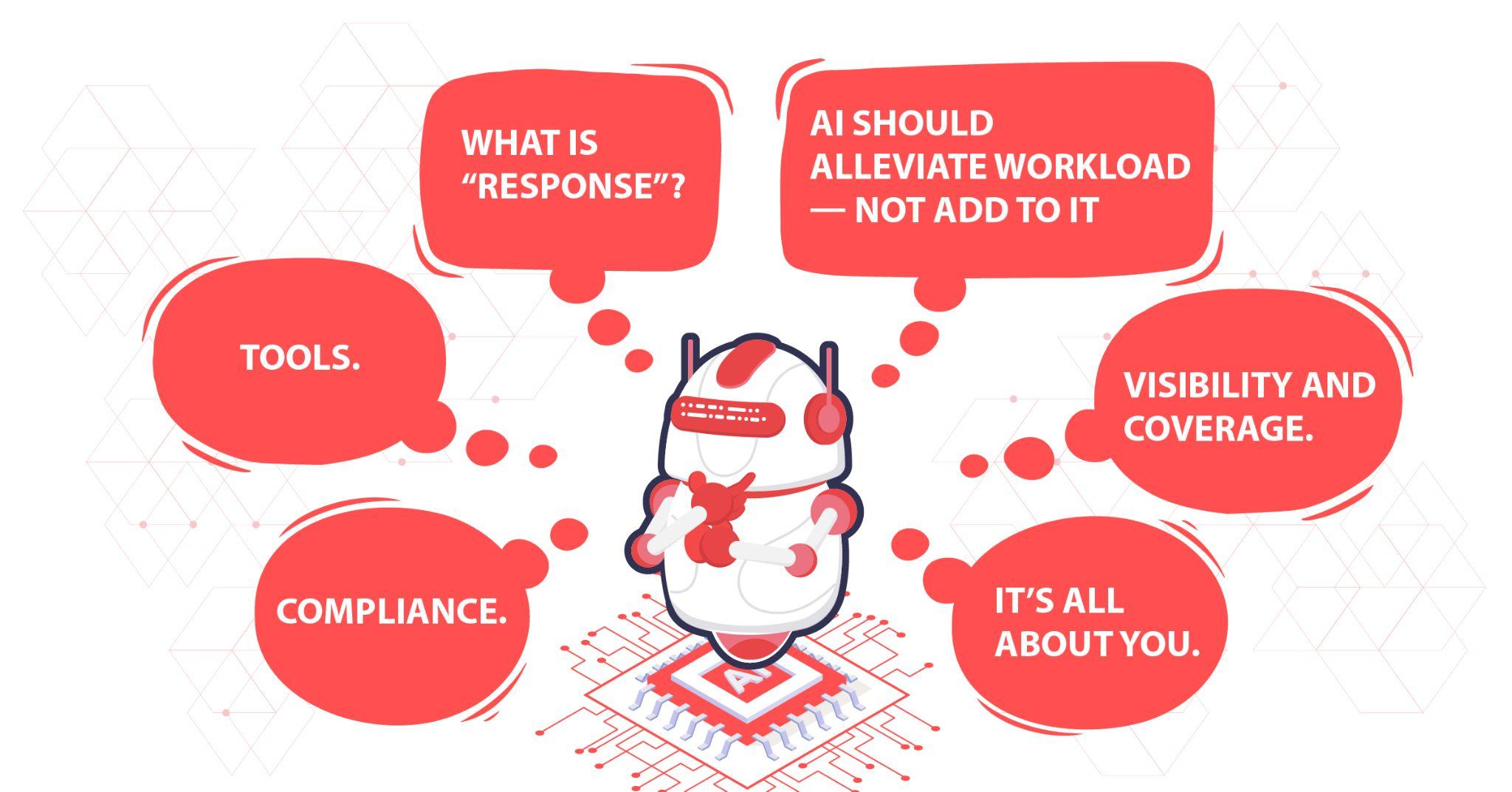

- What is “response”? “Response” is currently poorly defined among cybersecurity vendors as it can include anything from what basically constitutes as an alert to be handled by your in-house team, to the full recovery of your systems performed remotely.
Look for response technologies and services that fully perform investigations for you and show you the results within minutes for even the most sophisticated attacks. Make sure that those results are fully connected forensically across the entire organization into one cohesive complete understanding for each and every step of the attack. Also, make sure that a vendor provides a way to fully remediate attacks early on in the attack lifecycle.
- Artificial Intelligence should alleviate your workload—not add to it. Be careful of vendors that use AI for non-substantial subsets of tasks that inevitably push the majority of the workload of detection and investigation back to your analysts (i.e., we detected a lot of malicious activity, here is a ticket for each malicious process for you to go through).
Some solutions will give you a metric of confidence. Ask these providers to explain the difference between their solution’s 70% and 75% malicious ratings. Is this solution offering a sufficient level of automated triage, or is it just throwing the final decision back to the customer?
Ask potential vendors about their data and their ML methodology. Do any models need to be trained on-site; if so, for how long? Which types of detections tend to produce more false positives? Which types of detections are done without AI? How much of triage and investigations is automated? How often do you retrain? Also, how robust is the model against noise?
- Visibility and coverage. Be careful when seeing these words. All solutions detect, respond, and report back to you, and naturally, each vendor’s technology uniquely analyzes your data. However, how they present this data to you is important. The technology seeing the problem and you, the end user, seeing the problem via the technology are entirely different concepts.
Does visibility and coverage mean giving you access to TB of raw telemetry data? Raw telemetry is mostly useful for digital forensics incident response (DFIR) services and log data compliance—not for detecting and responding to live threats.
On the other side, APT-level attacks (which now include ransomware and supply chain attack campaigns) can go months without detection. Without telemetry generating security tools coupled with long-term data retention, researchers and responders (DFIR services) won’t have much to work with in a post-breach investigation.
Be sure to have your team that will be using this technology (as opposed to the buyers) evaluate the ease of use, actionability, and thoroughness of the platform dashboard. Is information presented in an actionable way for your team? What is the workflow like? How much friction is there in the UI and UX of the vendor’s platform? Does the platform present that entire attack storyline from initial access into your system or is the storyline segmented into individual processes on individual endpoints?
- Tools. If your organization hasn’t had the opportunity or resources to thoroughly develop your cybersecurity posture, you may want to strongly consider providers that offer a more comprehensive technology stack. If your organization already has access to tools, consider a provider offering tools with different utilities than yours. Most importantly, remember that tools from different vendors may not play nicely and have trouble integrating with tools or platforms from other vendors. Inquire about this and look into this when researching 3rd party reviews.
- Compliance. Although MDR focuses more on detection than compliance, many MDR vendors do offer services that help organizations meet compliance requirements, such as GDPR and CCA. As your organization grows, compliance—as well as cybersecurity—becomes more important and more complicated; it’s advisable to handle these issues early on to avoid trouble further down the road.
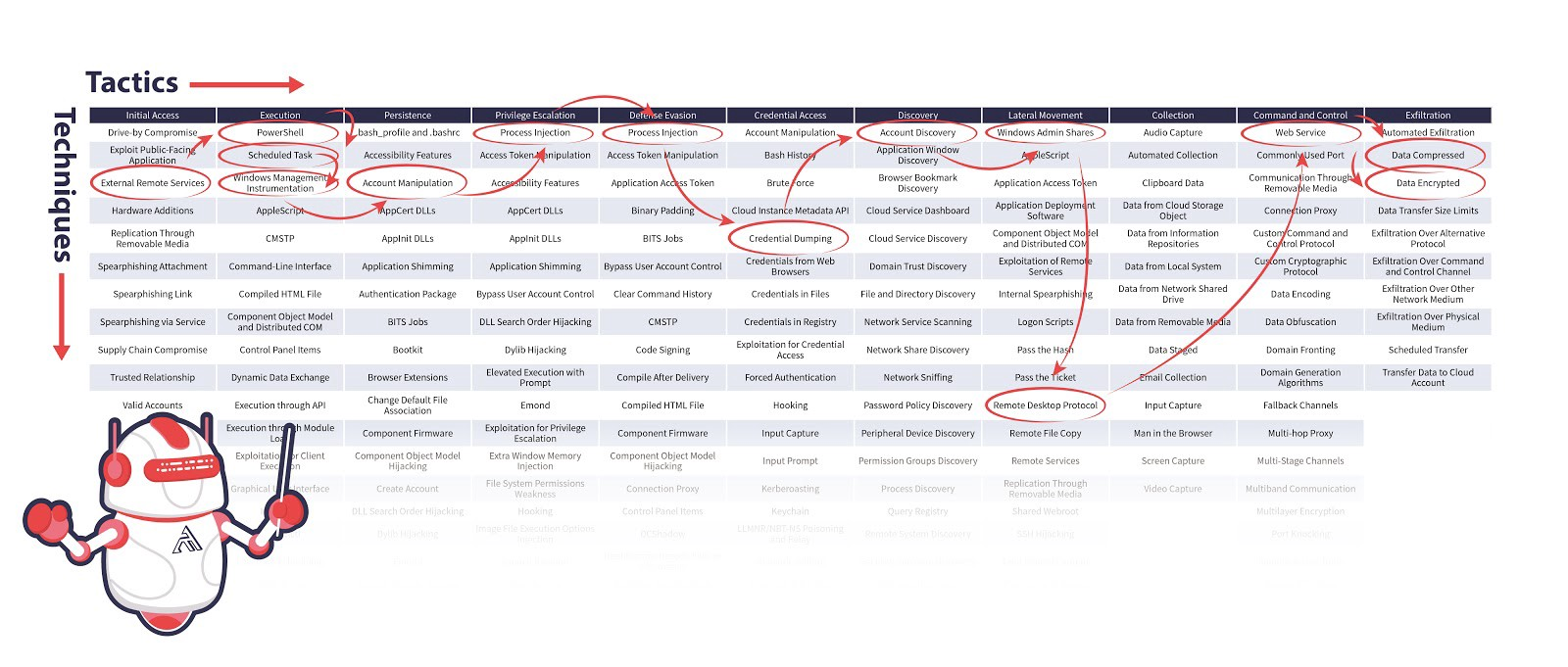
- It’s all about you. There are many questions that you need to know the answers to before you even begin evaluating MDR vendors. Here are a few. What is your current technology stack? What is your current coverage? Who are the major cyber threat actors targeting your industry? Who are the major threat actors targeting your geographical location? What are their common techniques and tactics? What is your current coverage in comparison to the active and emerging threat actors you listed? Have you mapped your defenses onto the MITRE ATT&CK and D3FEND framework? Are you familiar with the MITRE ATT&CK and D3FEND frameworks?
If you answered “no” to that last question, here is a quick reading list for you to get you up-to-date on the universal language used by all cybersecurity vendors.